The SSL certificates are essential for establishing a trusted connection between the different VMware Cloud Director Availability appliances and their proper service.
Each of them comes with their unique self-signed SSL certificate during the deployment. But still, these certificates need to be replaced when they expire, or if the providers prefer to use CA-signed ones to make sure there will be no browser warnings, for example.
This post will review the necessary steps to replace the Cloud Service, Manager Service, Replicator Service, and the Tunnel Service certificates with CA-signed ones.
- PKCS#12 (.pfx) certificate and the private key should use the same password
- PKCS#12 file should contain only one entry – the private key and its corresponding certificate and, optionally, the certificate trust chain
- RSA key size should be 2048-bit or larger
- The certificate should not use insecure hash algorithms like SHA1 or MD5
Command 1: Generate a new private key and Certificate Signing Request:
|
openssl req –out CSR.csr –new –newkey rsa:2048 –nodes –keyout privateKey.key |
Command 2: Convert .crt to .pem
|
openssl x509 –inform der –in certificate.cer –out certificate.pem |
Command 3: Prepare a PKCS#12 (.pfx) from a .pem (in case your CA didn’t provide it to you)
|
openssl pkcs12 –export –out certificate.pfx –inkey privateKey.key –in certificate.crt –certfile CACert.crt |
It is sufficient for most providers to use a CA-signed certificate for the Cloud Service only and self-signed certificates for all other services. This CA-signed certificate has to be generated for the public address of VMware Cloud Director Availability.
Steps
1. Login through SSH with the root user to the VMware Cloud Director Availability Cloud Service host.
2. Generate a new private key and Certificate Signing Request using the following command:
|
openssl req –out CSR.csr –new –newkey rsa:2048 –nodes –keyout privateKey.key |
3. Fill in the necessary data similar to this example
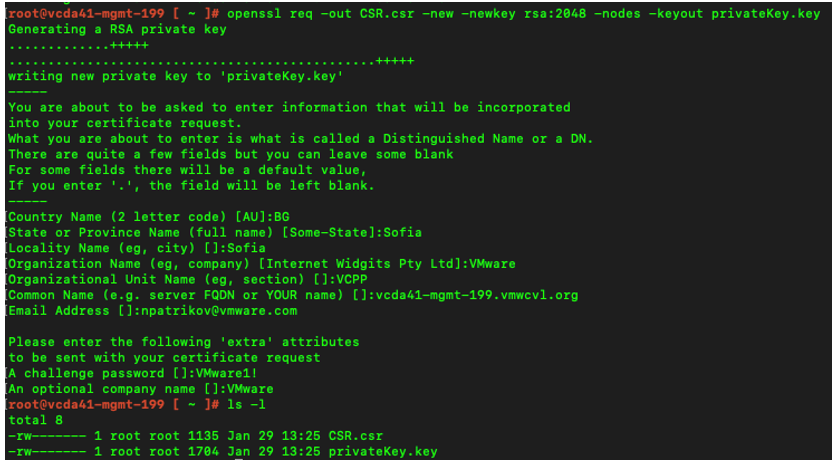
Figure 1: Generating a Certificate Signing Request
4. Once the CSR is generated, you need to transfer it to the CA for signing.
5. If the received CA-signed certificate is not in PKCS#12 format (.pfx), please use the following command to prepare it:
|
openssl pkcs12 –export –out certificate.pfx –inkey privateKey.key –in certificate.crt –certfile CACert.crt |
(where privateKey.key is the private key used for the CSR and CACert.crt is the CA certificate)
6. Load the certificate to the Cloud Service using:
A VMware Cloud Director Availability UI
-
- Navigate to the VMware Cloud Director Availability Cloud Service URL (https://Appliance-IP-Address/ui/admin.)
- Log in as root.
- Select Settings from the left pane called Configuration.
Figure 2: Settings in Configuration menu
-
- Under Appliance Settings, you will find Certificate.
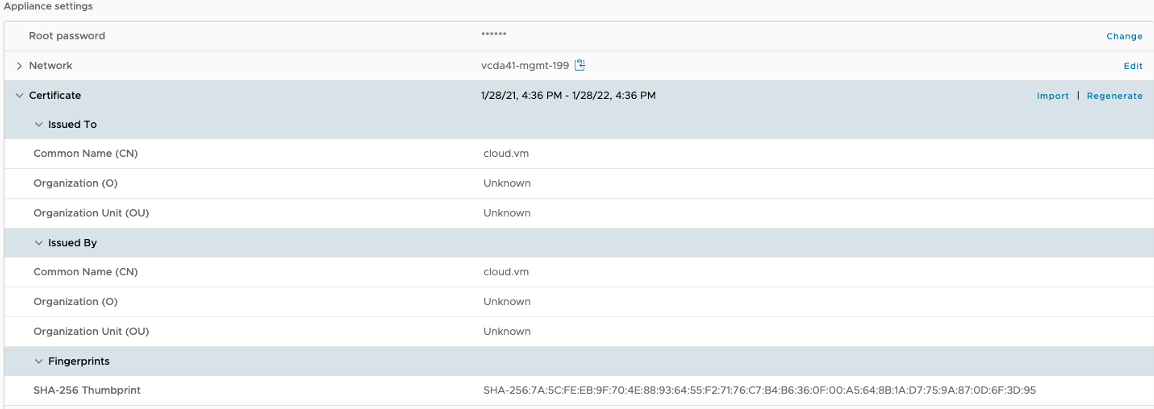
Figure 3: Certificate information in Settings
-
- Click Import.
- Fill in the Export Password (specified while creating the .pfx).
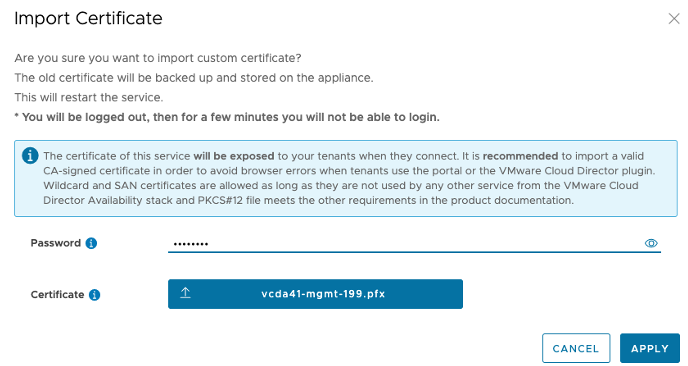
Figure 4: Importing a certificate
-
- Click Apply.
B VMware Cloud Director Availability API through command-line
-
- Transfer the .pfx file to the VMware Cloud Director Availability Cloud Service host.
- Log in as root through SSH to the VMware Cloud Director Availability Cloud Service host.
- Log in as root to the VMware Cloud Director Availability API through the command-line using:
|
c4 loginroot ‘password’ |
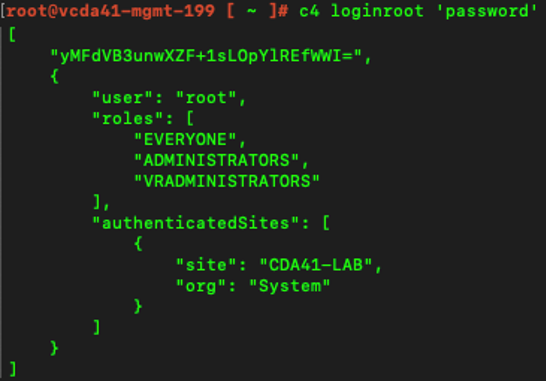
Figure 5: Authenticating through the command-line
-
- Upload the new certificate using:
|
c4 upload_certificate /path/to/cert/cert.pfx ‘Export password’ |
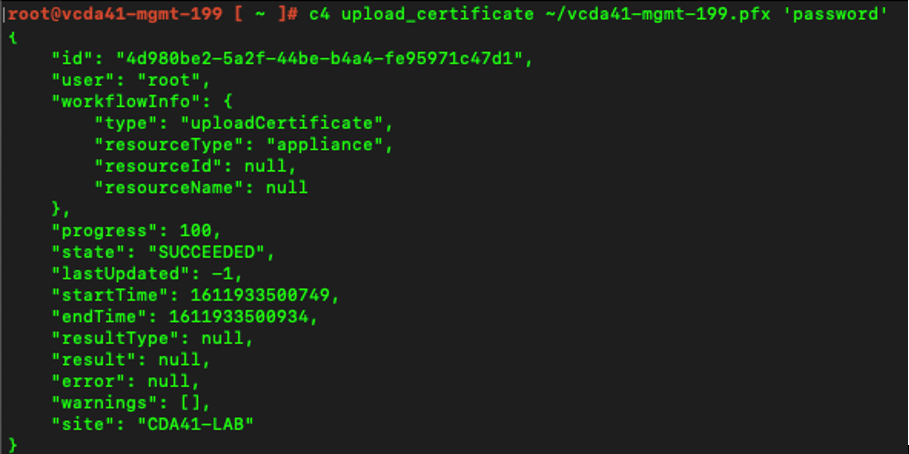
Figure 6: Importing a certificate through the command-line
-
- The VMware Cloud Director Availability Cloud Service will be restarted after the certificate change
- You will no longer see any warnings in the browser.
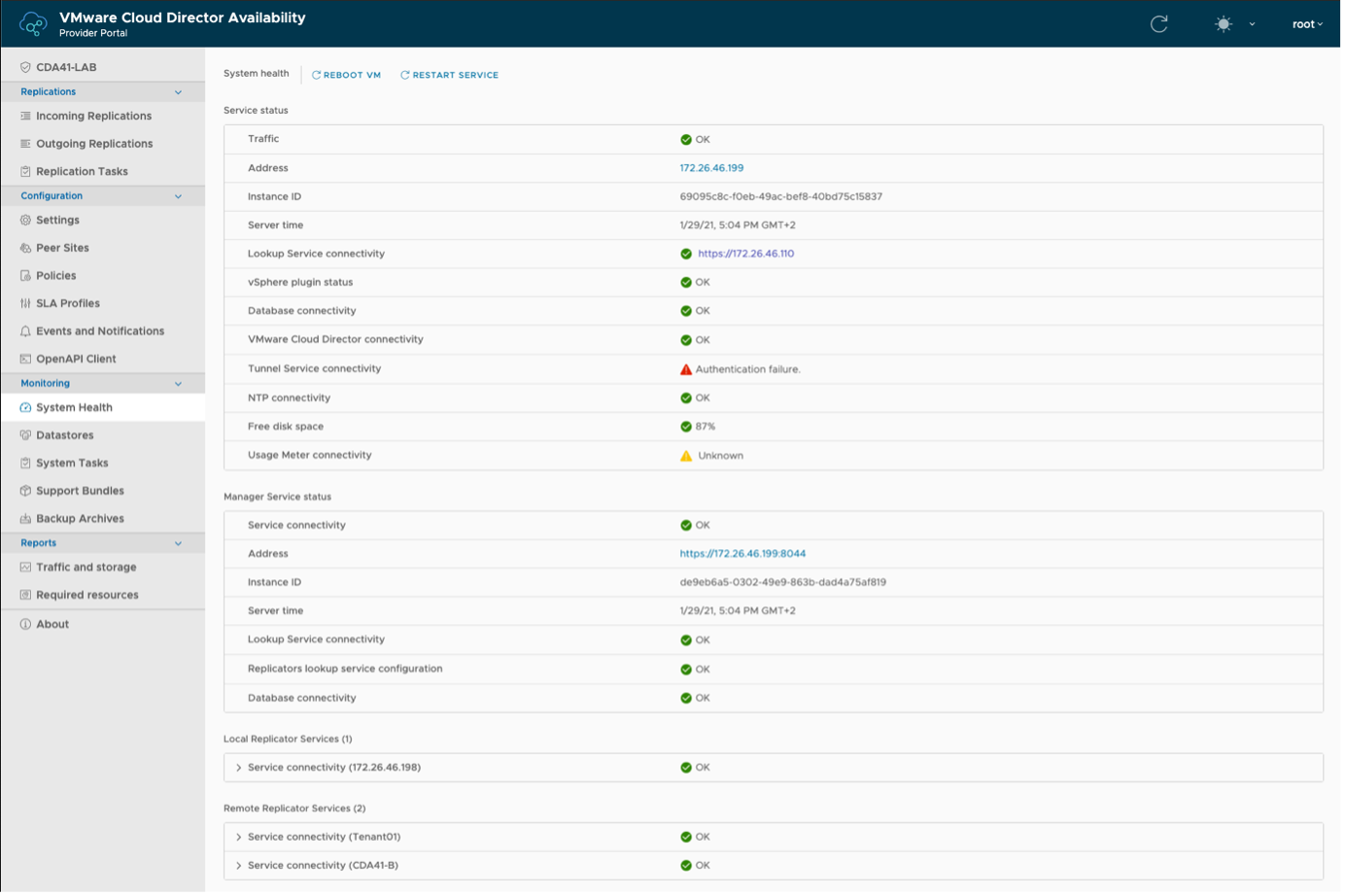
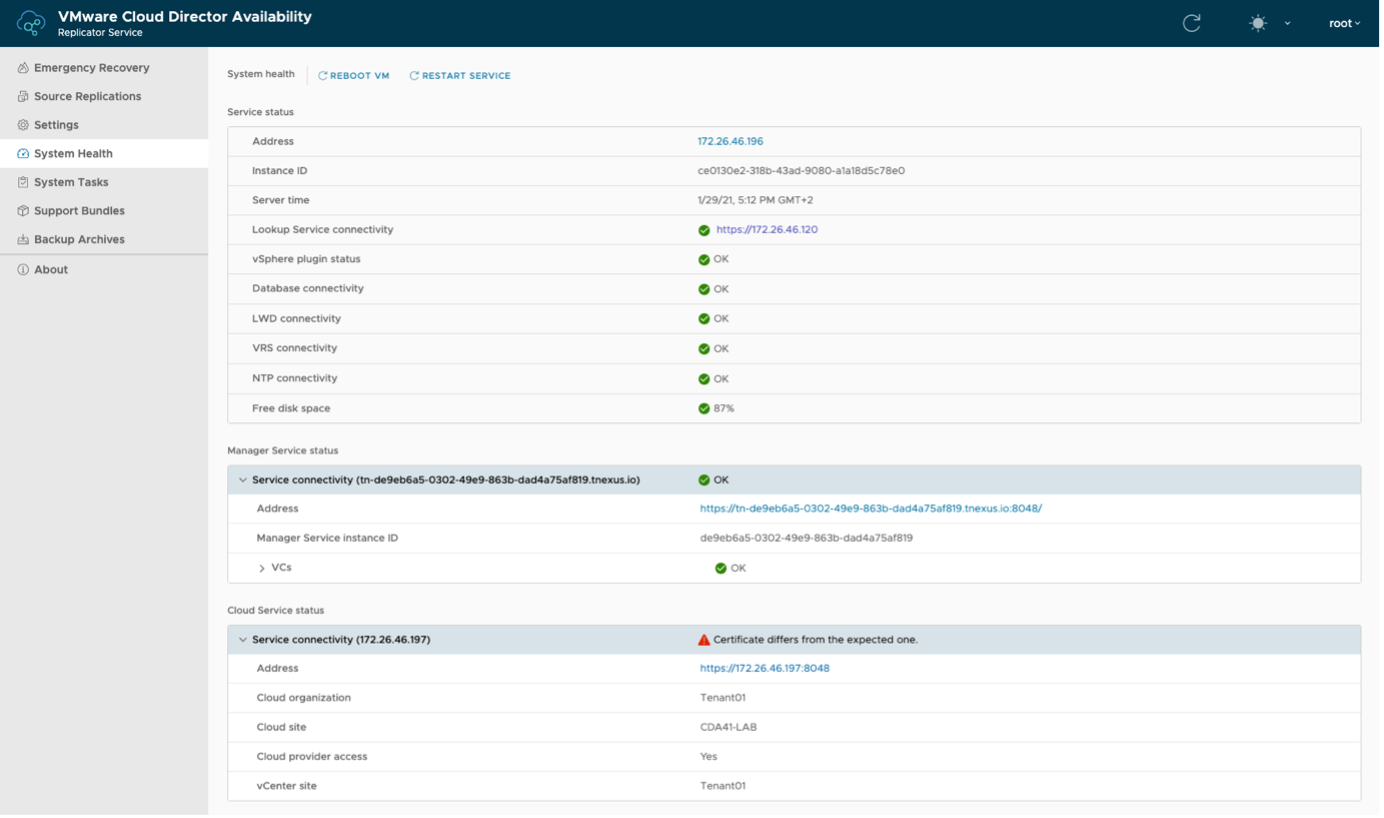
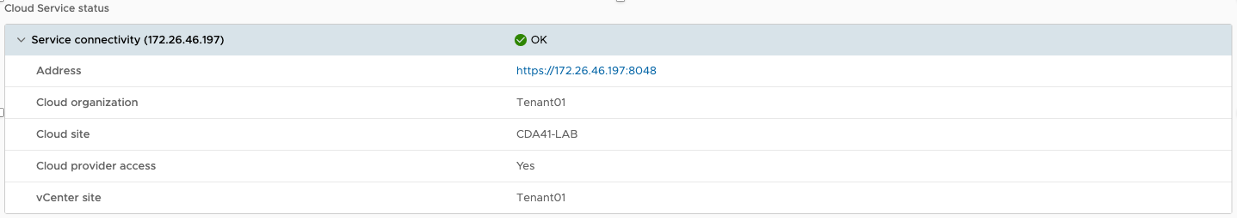
To see what other services are affected by the change and fix, you can open System Health under Monitoring in the left pane.
You can see that the connectivity to the Tunnel Service is showing failure.
To fix it, you need to perform the steps in Procedure 1.
Procedure 1:
- Click on Settings under Configuration.
- Find Tunnel Service address in Service Endpoints.
- Click Edit.
- Enter the root password.
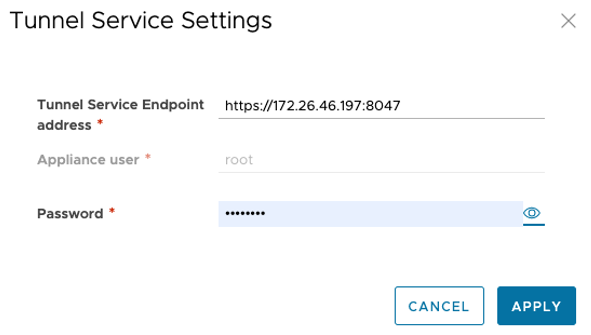
- Click Apply.
- Accept the certificate request.
- Go back to System Health and check that the connectivity to the Tunnel Service is okay.
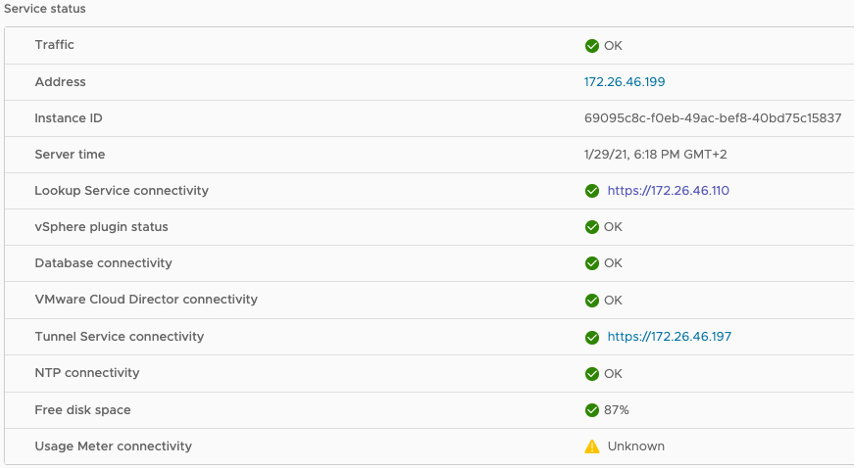
Such a certificate change impacts both cloud and on-premises sites that are paired to this Cloud Service. In order to restore the regular operation, you will need to re-pair all connected sites.
On-premises
To re-pair with an on-premises site, your tenant needs to:
- Open the VMware Cloud Director Availability on-premises appliance URL.
- Log in as root.
1. Click on Settings in the left pane.
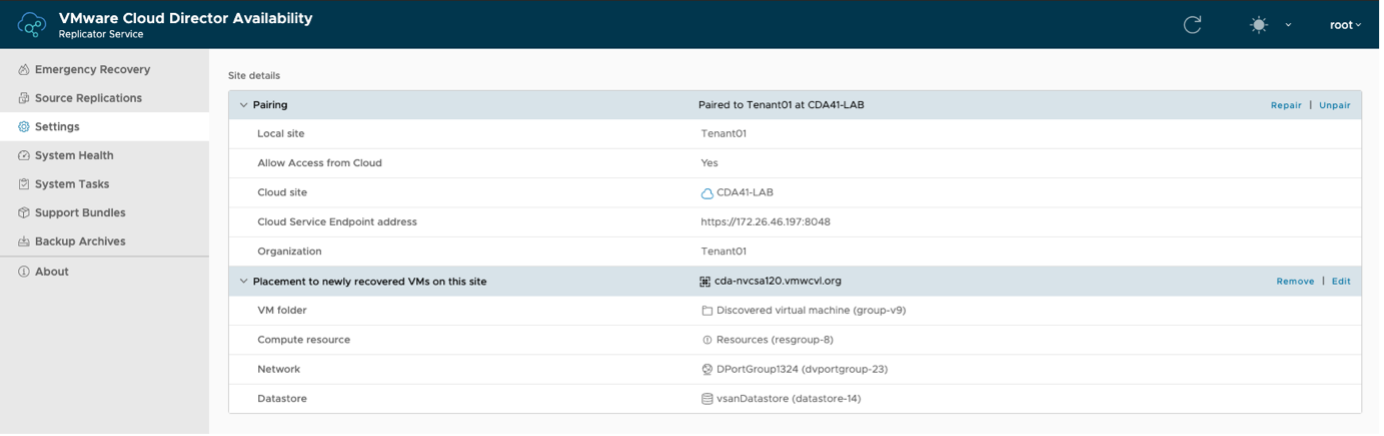
2. Find Pairing under Site Details.
3. Click Repair.
4. Enter all information in the wizard and accept the certificate request.
5. Finish the wizard.
Cloud
To re-pair with a cloud site, the remote cloud site admin needs to:
- Open the VMware Cloud Director Availability UI of the remote site.
- Log in as root.
- Click Peer Sites under Configuration in the left pane.
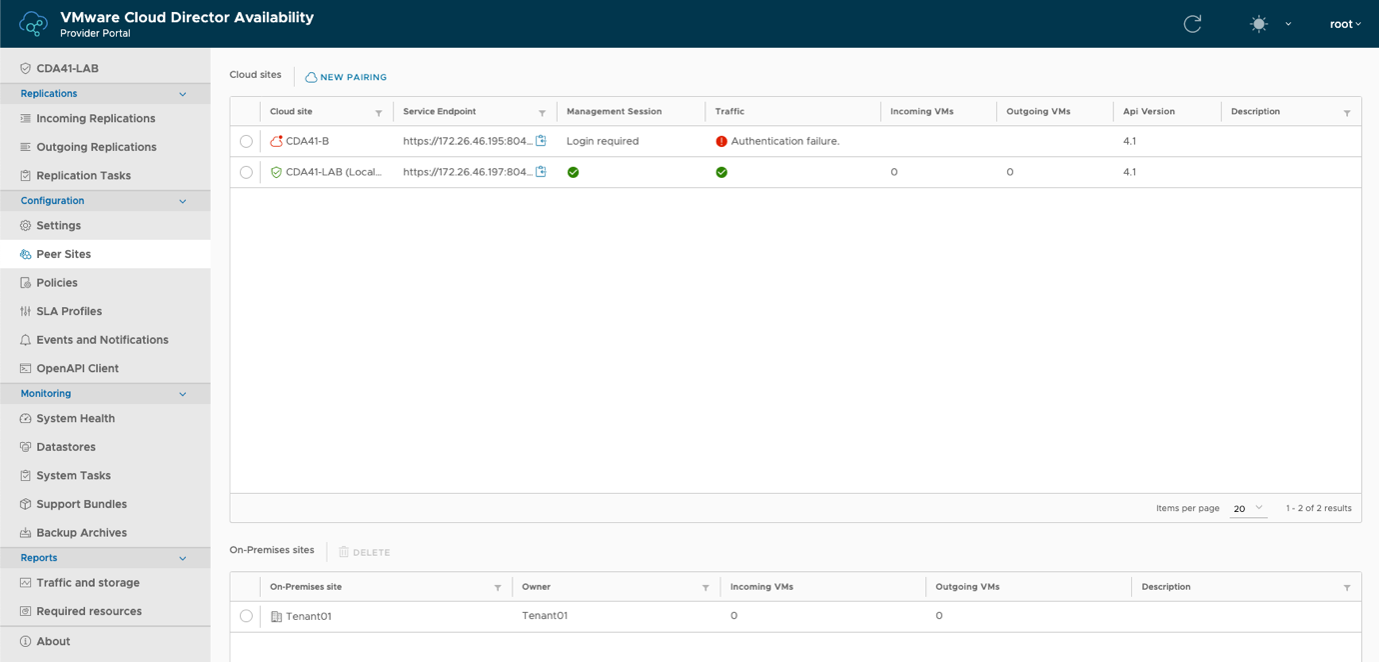
4. Select the cloud site with the changed certificate (marked with an error).
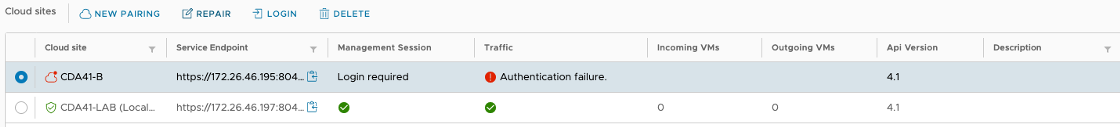
5. Click Repair.
6. Click Update and accept the certificate request.
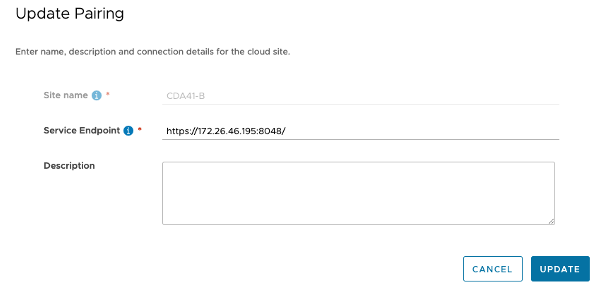
Figure 18: Updating the pairing configuration
7. A message indicates there are actions to be performed on the other site.
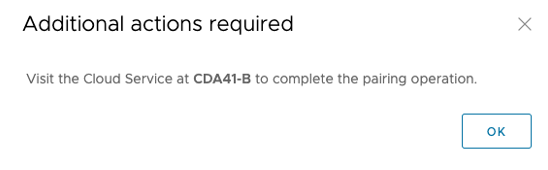
Once these steps are performed, you need to do the same at the local site.
If you plan to replace all self-signed certificates with CA-signed ones, you can follow the steps described for the Cloud Service. The only difference is in the affected services as follows:
- When changing the SSL certificate of a Manager Service, the trust between all Replicator Service instances is invalidated. To re-establish it, you need to register all Replicator Service instances by performing Repair from their UI and re-pair the cloud sites.
- When changing the SSL certificate of a Replicator Service, it leads to a paring problem with Manager Service. You need to re-pair to the Manager Service on the local site and re-establish the trust between all cloud sites.
- When changing the SSL certificate of a Tunnel Service, you need to re-establish the connectivity between it and the Cloud Service. To do so, you can perform Procedure 1. For about 30 minutes, you might see a Generic error occurred during TLS handshake message, but you do not need to perform any actions to fix it. The reason is that the certificate replacement restarts the service, which breaks the sessions with the remote cloud or on-premises replicator. The session initiation happens every 30 minutes, which means that all remote sites should auto-recover pairing in no longer than 30 min.
- When changing the VMware Cloud Director SSL certificate, you need to re-establish the trust connection from the VMware Cloud Director Availability Cloud Service UI.
- When changing the Lookup Service SSL certificate, all VMware Cloud Director Availability appliances need to trust the Lookup Service certificate once again.
One of the new features in VMware Cloud Director Availability 4.1, which enables backing-up all appliances, is very useful when planning to perform changes to any of the services.
Considering that replacing the certificates impacts the operation of VMware Cloud Director Availability, we always recommend generating a backup before proceeding with any of the steps for updating the SSL certificates. You can see how in this blog post.