Container Service Extension (CSE) version 1.2.6 introduced a key enhancement, role-based access control (RBAC). The new feature gives service providers the ability to monetize Kubernetes service offerings by selectively enabling tenant access to CSE. A tenant admin can then use the role-based access control to assign Kubernetes operator roles within their organization.
Role-based access control allows the service provider to propagate the right to create, modify and delete K8s clusters to individual organizations. Tenant admins then add the right to new or existing roles for their users. Once role-based access control is enabled, only users that have the proper right can run the cluster create|delete and node create|delete commands of CSE (existing clusters can still be accessed, but not modified).
Find the Release Notes here: https://vmware.github.io/container-service-extension/RELEASE_NOTES.html
The main repository for CSE on github: https://github.com/vmware/container-service-extension
The main documentation page: https://vmware.github.io/container-service-extension/INTRO.html
Contents
Upgrade procedure for Container Service Extension (CSE)
To upgrade CSE to the latest version, follow the procedure documented in the “Server Upgrade” section: https://vmware.github.io/container-service-extension/CSE_ADMIN.html#serverupgrade
- Gracefully stop the CSE server
- Reinstall cse using pip:
pip3 install —user —upgrade container–service extension
- IMPORTANT: If you upgrade from CSE version 1.2.5 or lower, make sure to add the new parameter for RBAC in the config.yaml file: “enforce_authorization” under the “service” section, set to “true” or “false”.
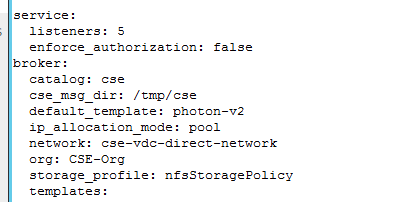
- Re-register CSE with vCD:
cse install —config config.yaml
This will register CSE again as extension to vCD, and create the new privileges in vCD that are used for role-based access control. - Start the CSE server:
systemctl start cse
Propagate Privileges to a Tenant
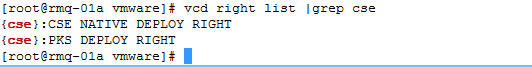
After enabling role-based access in config.yaml, a service provider can use the newly created right {cse}:CSE NATIVE DEPLOY RIGHT to allow a tenant to create and delete Kubernetes clusters in their Org. For that, use e.g. the vcd cli to add the right to the tenant org:
|
vcd right add –o CSE–Org “{cse}:CSE NATIVE DEPLOY RIGHT” |
Then an org admin can use the right to create new a new role, or add it to an existing role. A tenant user that has the role assigned can use the regular cse commands to create and delete clusters.
Learn More About the New RBAC Feature
For more information, refer to the RBAC section in the documentation: https://vmware.github.io/container-service-extension/RBAC.html