What are the best WordPress Security plugins and how to set them up the best way
What are the best WordPress Security plugins and how to set them up the best way…

What are the best WordPress Security plugins and how to set them up the best way…

The Most Important Stages and Plugins for WordPress Website Development Developing a WordPress website requires careful…
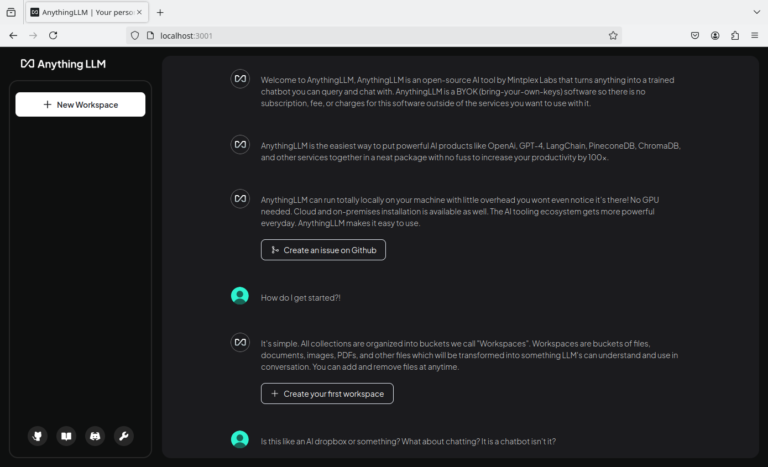
This post is part of a series on locally using AI models. Previous posts are Running…
Elasticsearch is a powerful, open-source search engine and analytics platform for storing, searching, and analyzing large…

In today’s fast-paced tech world, partners need every advantage to stay competitive. The CloudLinux Partner Program…

We are excited to announce the release of the updated WHMCS plugin, version 1.3.17. This latest…

Drupal 11 is early! But don’t panic, the new Drupal 10 support model means you are…
The client manufactures and installs facade materials and elements: sidings, panels, tiles, shingles, and gutters. On…

WebPros is excited to launch WP Squared, a revolutionary WordPress hosting solution, and CloudLinux is equally…
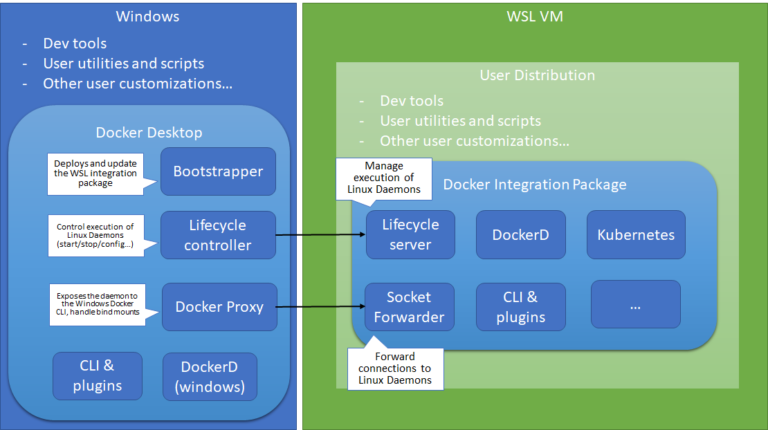
March 2, 2020 by Matt Hernandez, @fiveisprime Last June, the Docker team announced that they will…
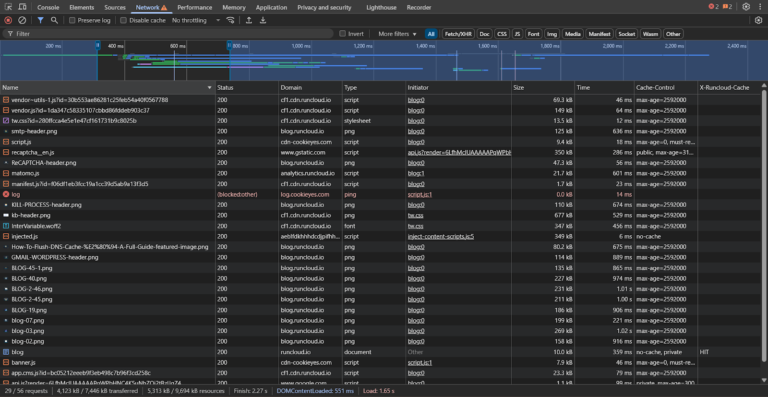
A slow WordPress site isn’t just frustrating – it drives visitors away and hurts your SEO….

Managing a modern Linux environment is complex. Virtual machines and containers are spread across on-premises data…
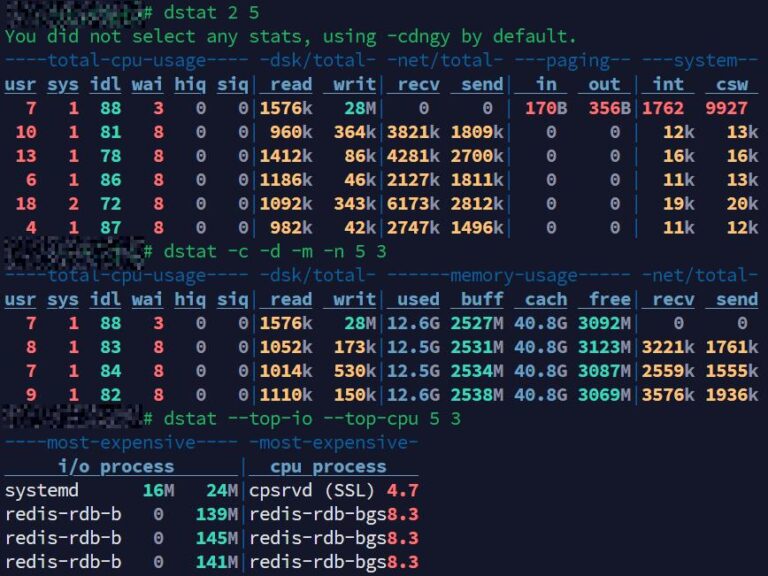
Servers can sometimes appear idle yet still perform sluggishly. This scenario is common across web hosting…

Customer churn in hosting is not always about pricing. More often, it is driven by technical…
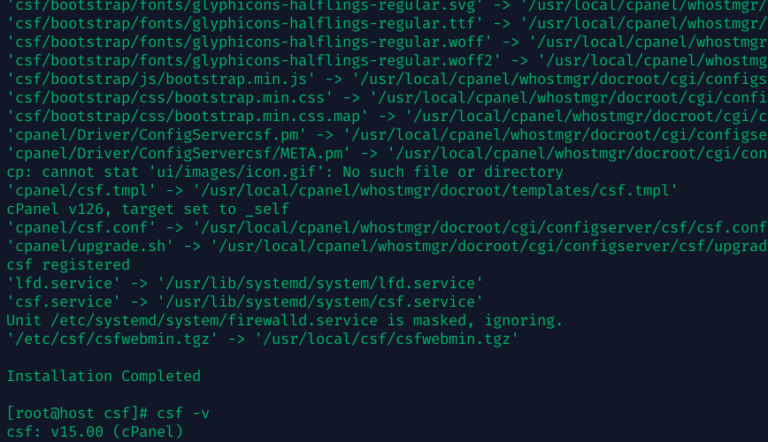
Update: CSF Project Status (January 2026) – Since the original publication of this article, there have been…
Welcome to the RunCloud 2025 Year in Review. First of all, Happy New Year! Here’s to…

SUSE has certified and is currently certifying various cryptographic modules for FIPS 140-3 on SUSE Linux…

What if your servers crashed during your biggest sales event of the year? For enterprise IT…

CloudLinux Product Pulse is a new webinar series designed to give our customers and partners an…
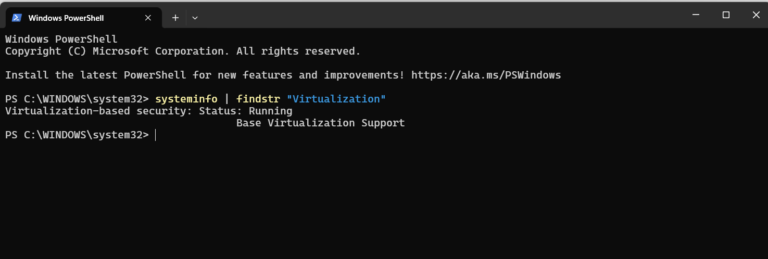
Although Linux remains the easier and more efficient platform for most containers, Windows Server still plays…

The countdown to Mobile World Congress 2026 has begun, and the industry is buzzing with the…
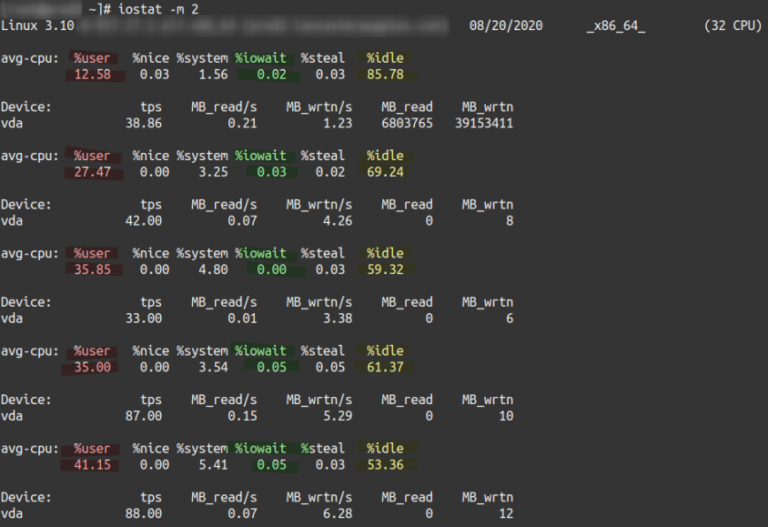
iowait (wait, wa, %iowait, wait%, or I/O wait) is often displayed by command-line Linux system monitoring tools…

Choosing a switch can feel deceptively simple, until slow file transfers, port shortages, and similar unexpected…
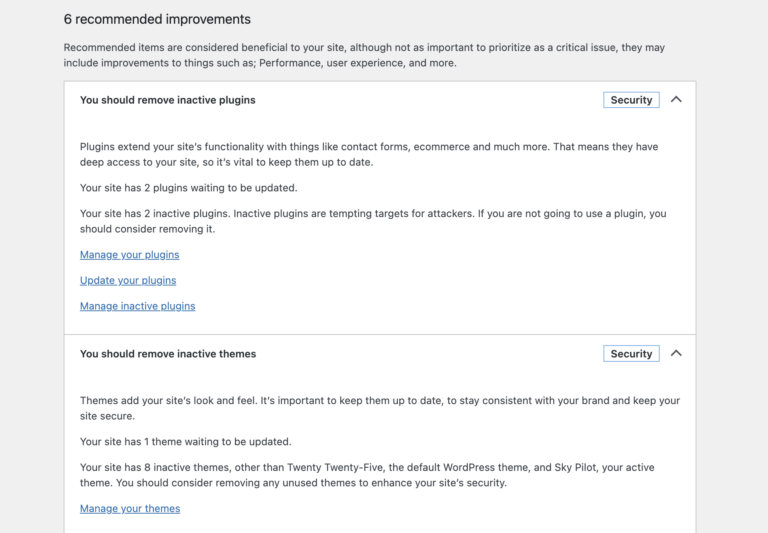
Unused WordPress plugins can slow your site down and weaken your security, even when they’re deactivated….

Note: This article serves as an overview and index, connecting you to previous detailed PHP optimization…
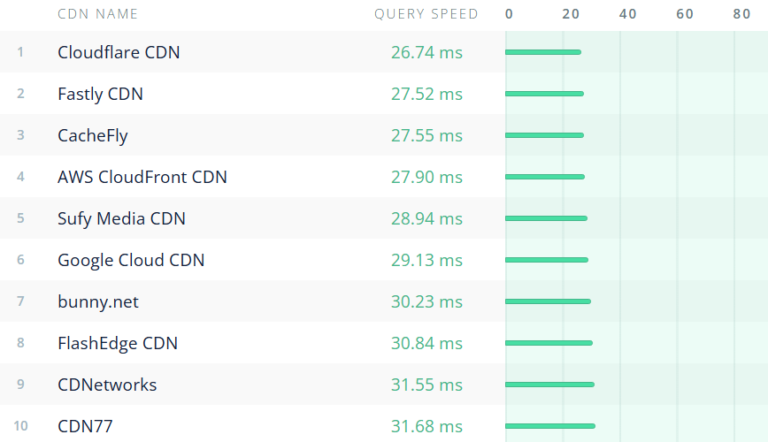
Content delivery networks (CDNs) are crucial in ensuring fast and reliable access to digital content across…
Raspberry Pi board has earned its reputation as one of the most versatile and capable single-board…
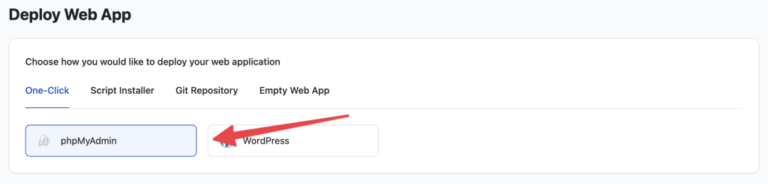
We are happy to bring One-Click phpMyAdmin feature in RunCloud for you. Using this new feature,…

At CloudLinux, we’re committed to building performance solutions that help hosting providers run websites faster and…

Choosing a rolling release Linux distribution means you get the latest software without having to reinstall…

Like the amber in “Jurassic Park,” immutable Linux distros safeguard the core system. Here’s a story…