Why We’re Putting Partners at the Heart of SUSECON 26
In B2B technology, “resilience” is often discussed in terms of code, clusters, and clouds. But after…

In B2B technology, “resilience” is often discussed in terms of code, clusters, and clouds. But after…
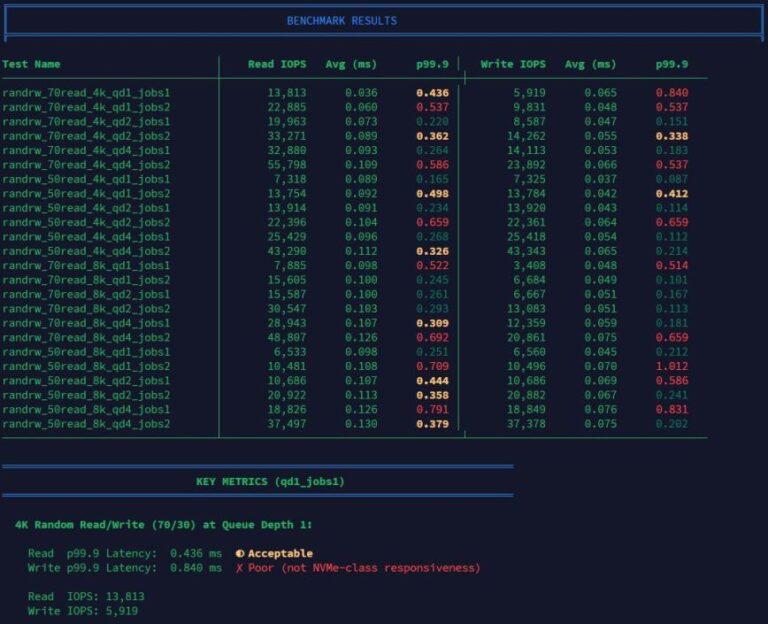
Every VPS provider loves to advertise NVMe storage. It sounds fast on paper and is usually…

Enterprises are embracing AI at an incredible pace—and that’s exciting! However, this rapid adoption creates significant…

Servers aren’t what they used to be. If you’ve spun up a small VPS (Virtual Private…
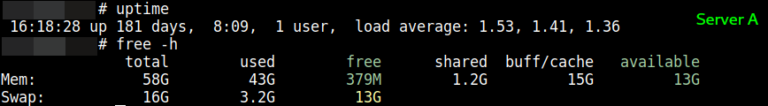
At times, we need to know precisely how a Linux system is using memory. This article…

We are announcing the beta release of Per-Site CageFS Isolation, a new feature designed to enhance…

Managing a modern Linux environment is complex. Virtual machines and containers are spread across on-premises data…
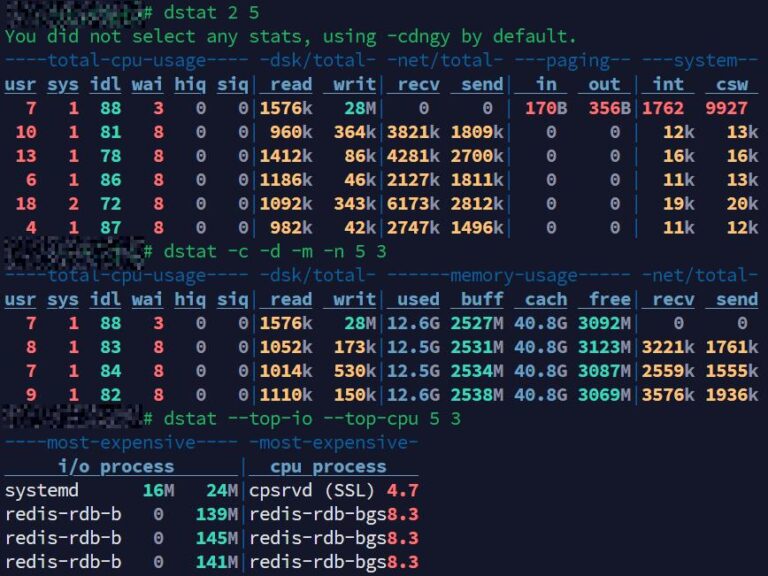
Servers can sometimes appear idle yet still perform sluggishly. This scenario is common across web hosting…

Customer churn in hosting is not always about pricing. More often, it is driven by technical…
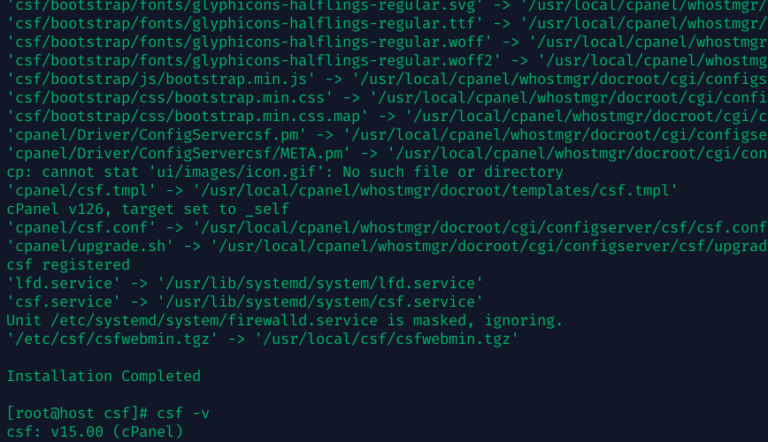
Update: CSF Project Status (January 2026) – Since the original publication of this article, there have been…

SUSE has certified and is currently certifying various cryptographic modules for FIPS 140-3 on SUSE Linux…

What if your servers crashed during your biggest sales event of the year? For enterprise IT…

CloudLinux Product Pulse is a new webinar series designed to give our customers and partners an…

The CloudLinux gradual rollout slot 6 for the package kernel-4.18.0-553.89.1.lve was paused due to potential bug reported…

The countdown to Mobile World Congress 2026 has begun, and the industry is buzzing with the…
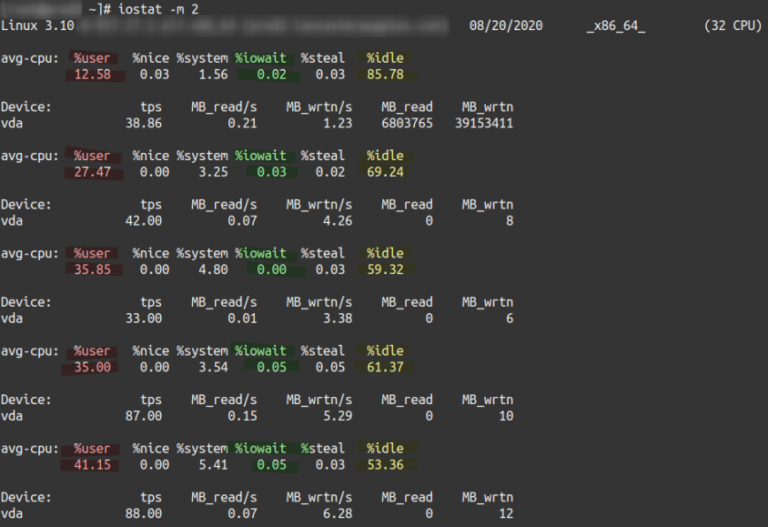
iowait (wait, wa, %iowait, wait%, or I/O wait) is often displayed by command-line Linux system monitoring tools…

Choosing a switch can feel deceptively simple, until slow file transfers, port shortages, and similar unexpected…

Note: This article serves as an overview and index, connecting you to previous detailed PHP optimization…
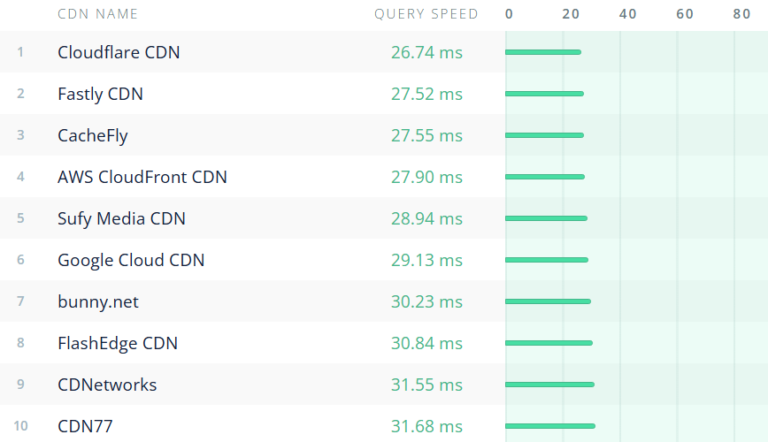
Content delivery networks (CDNs) are crucial in ensuring fast and reliable access to digital content across…
Raspberry Pi board has earned its reputation as one of the most versatile and capable single-board…

At CloudLinux, we’re committed to building performance solutions that help hosting providers run websites faster and…