How to Check if TCP Port is Open, Closed or in Use on Linux?
When working with networking services, you might encounter networking ports on Linux. But have you ever…
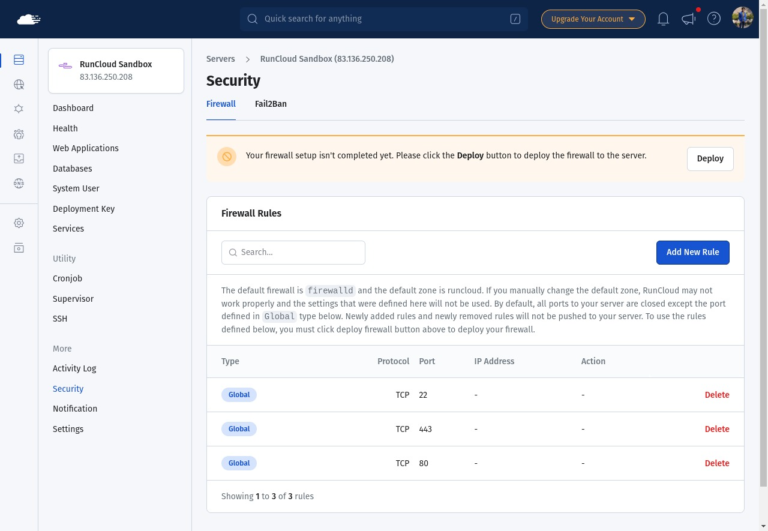
When working with networking services, you might encounter networking ports on Linux. But have you ever…

Thousands of flights were canceled, leaving travelers stranded during the peak summer travel season. Airports turned…

Drupal 11 is early! But don’t panic, the new Drupal 10 support model means you are…
![5 Ways to Fix the SSH Connection Refused Error [SOLVED]](https://linuxpunx.com/wp-content/uploads/2024/07/5-ways-to-fix-the-ssh-connection-refused-error-solved-768x514.png)
When managing your servers, you will often need to use the Secure Shell (SSH) protocol, but…

Today is a special day at SUSE: We are launching the next generation of SUSE Manager…
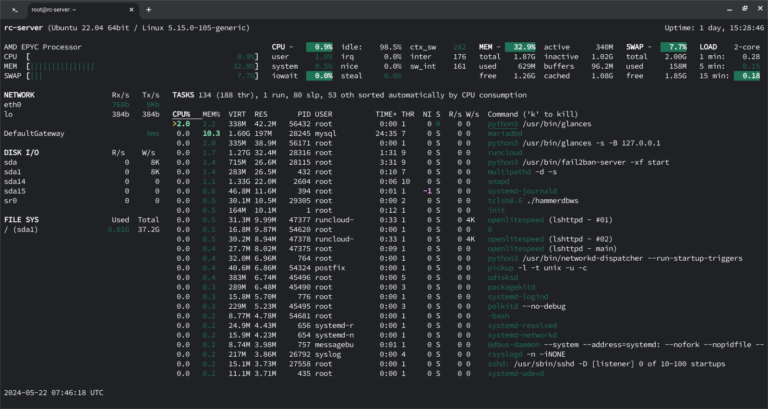
When it comes to monitoring system resources on Linux, htop has been the go-to tool for…
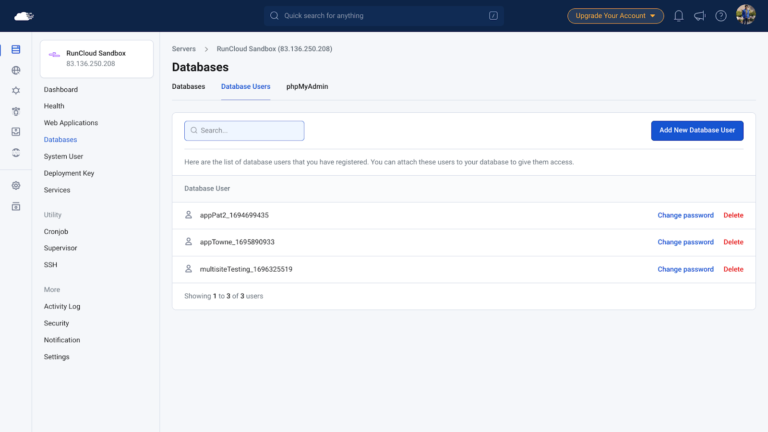
PHP and SQL are two of the most commonly used tools in web development. PHP is…

Navigating the end-of-life for CentOS has left the future of many organizations’ Linux uncertain, as they…

Amid changing market conditions and hyper-competitive landscapes, heterogeneity in your Linux estate isn’t just a reality;…

In today’s container-centric landscape, the Operating System (OS) is more important than ever. While containers and…

In today’s fast-paced business landscape, ensuring the seamless operation and availability of critical systems is paramount….

If you’re a marketer, you know how much content cloning can simplify your life. It lets…
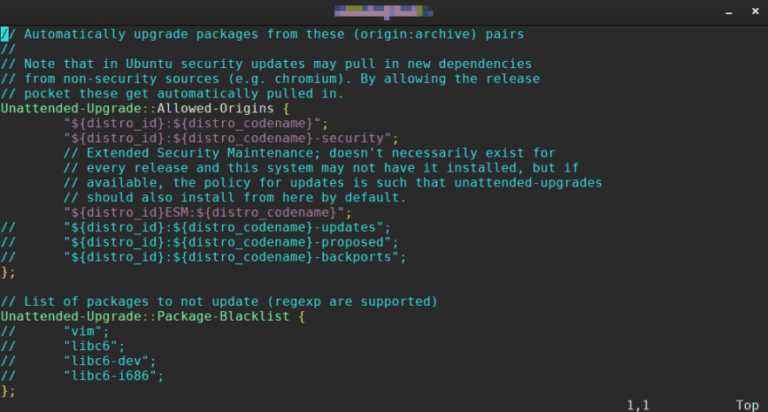
Linux server security is of critical importance to sysadmins. One central part of keeping Linux servers…
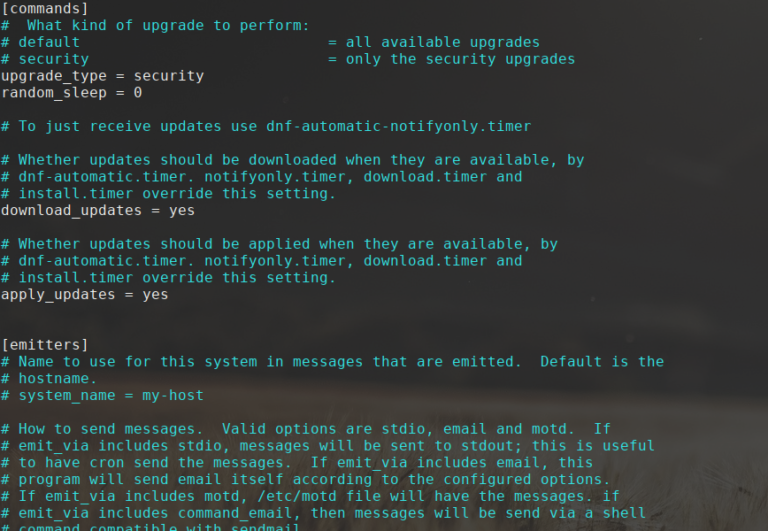
Linux server security is crucial to Linux server administration. Part of keeping Linux servers secure is…
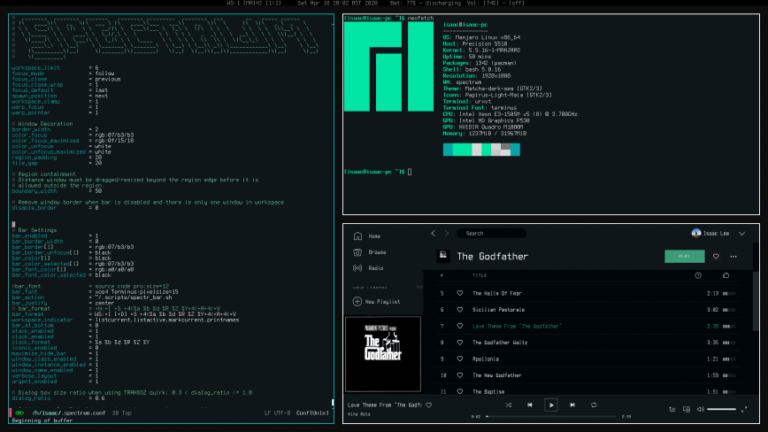
Are you searching for the best Linux distro (distribution) and DE (Desktop Environment) combination? What better…

This article has been contributed by Tanja Roth, Project Manager at the SUSE Documentation Team. It…

CentOS 7 has reached its end of life (EOL), and businesses that have relied on this…

June 30, 2024, marked the end of life (EOL) for CentOS 7. This critical milestone means…

Navigating the complexities of modern IT environments demands a partner who seamlessly integrates with your team,…

The end-of-life (EOL) date for CentOS 7 passed on June 30, 2024, and with this milestone,…

Krumware has been awarded the Rising Star Emerging Technology Solutions Partner of the Year at the…