ADVERTISEMENT

SSH is a client and server protocol, and it helps us to securely access the remote system over the network through the encrypted tunnel. SSH has a built-in file transfer mechanism (SCP) to transfer files and directories over the network, and it is way more secure than FTP (File Transfer Protocol).
In larger environments, it is a pain to enter the password every time to access remote machines. So, to ease the login, we can use SSH passwordless feature to access the remote machine without entering the password.
Here, we will see how to setup SSH passwordless login on CentOS 8 / RHEL 8.
Assumptions
Contents
Here we have two machines with two different usernames.
| Hostname | IP Address | User | OS | Purpose |
|---|---|---|---|---|
| server.itzgeek.local | 192.168.0.10 | raj | CentOS 8 / RHEL 8 | Source Machine |
| client.itzgeek.local | 192.168.0.20 | ram | CentOS 8 / RHEL 8 | Destination Machine |
Here, I will be using a hostname instead of an IP address.
Follow the steps to create the passwordless login.
Setup SSH Passwordless Login on CentOS 8
To enable the SSH passwordless login, we have to put the public key entry of the local machine on the remote machine’s ~/.ssh/authorized_keys (~ represents the user’s home directory) file.
We can set up an SSH passwordless login in two ways. Choose any one of the ways.
- Using ssh-copy-id Command
- Copying Keys Manually
Using ssh-copy-id Command
This method involves generating an SSH key pair on the source machine and place it on the destination machine with a single command (ssh-copy-id).
The ssh-copy-id command appends the generated SSH public key to existing keys in ~/.ssh/authorized_keys file on the destination. If ~/.ssh/authorized_keys file is not present on the destination machine, the command would create it and place SSH public key.
Generate Public Key
Log in to the source machine and create an SSH key pair using the following command.
[raj@server ~]$ ssh-keygen
Output:
Generating public/private rsa key pair. Enter file in which to save the key (/home/raj/.ssh/id_rsa): Created directory '/home/raj/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/raj/.ssh/id_rsa. Your public key has been saved in /home/raj/.ssh/id_rsa.pub. The key fingerprint is: SHA256:8BuI21rECULGQMs3BtU2o3jHyHghg+p5RE8naQTQP2A raj@server.itzgeek.local The key's randomart image is: +---[RSA 2048]----+ |+**o+.. | |o=+E X . | |.oX+& * | |.ooO.X = | |. = o * S | | o . + o | | . . o . | | o | | . | +----[SHA256]-----+
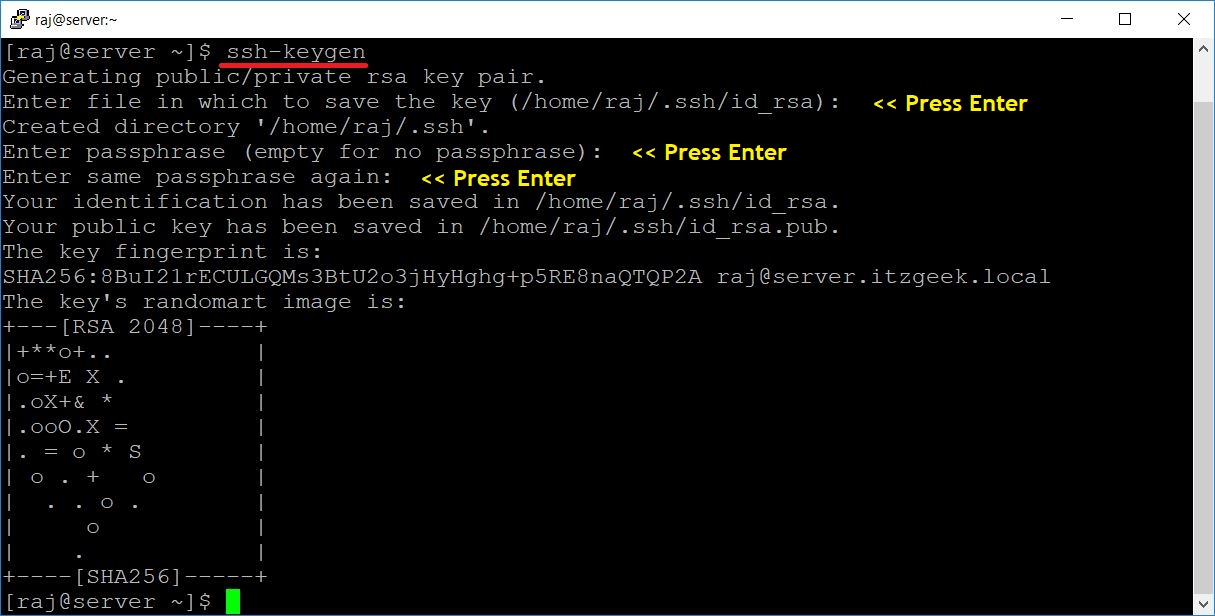
Once you have created, you will find two files id_rsa and id_rsa.pub inside the .ssh directory. We are going to use id_rsa.pub (public key) for SSH passwordless login.
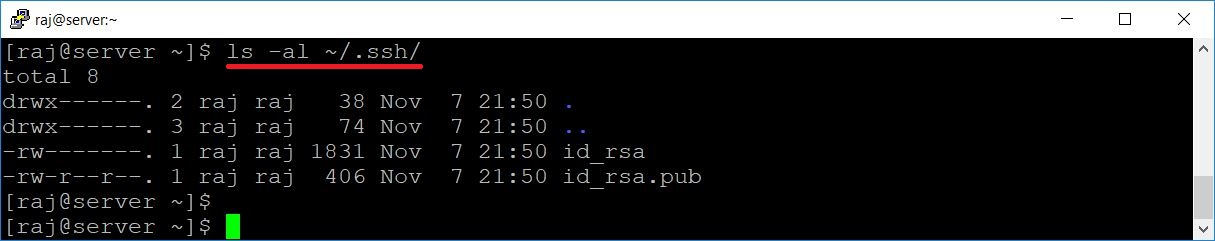
[raj@server ~]$ ls -al ~/.ssh/
Output:
total 8 drwx------. 2 raj raj 38 Nov 7 21:50 . drwx------. 3 raj raj 74 Nov 7 21:50 .. -rw-------. 1 raj raj 1831 Nov 7 21:50 id_rsa -rw-r--r--. 1 raj raj 406 Nov 7 21:50 id_rsa.pub
Copy Public Key
Use the ssh-copy-id command that comes with the openssh-clients package with an input file of id_rsa.pub.
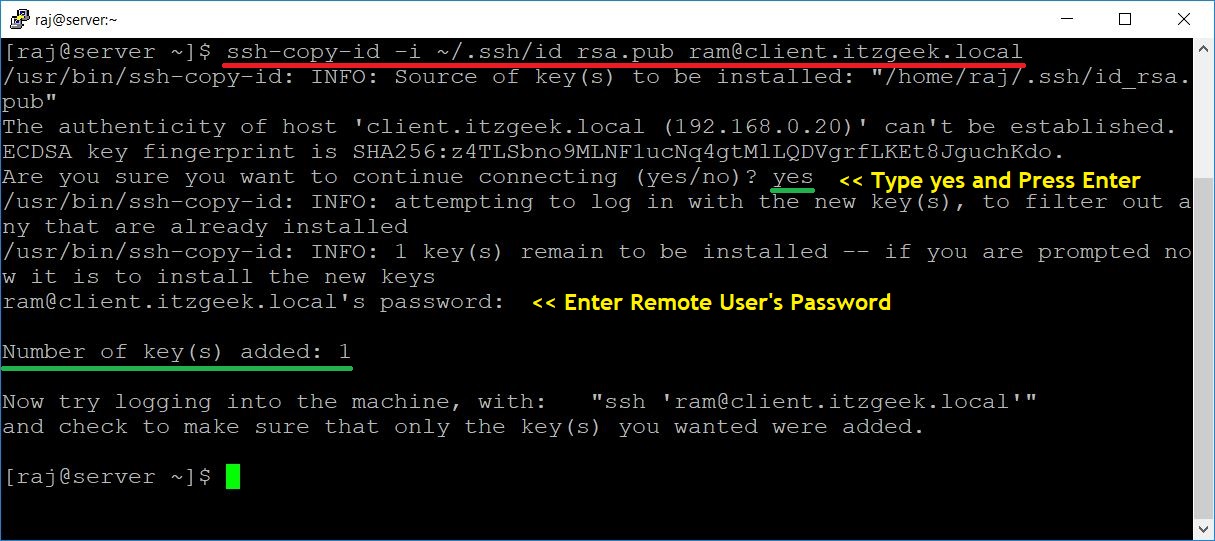
[raj@server ~]$ ssh-copy-id -i ~/.ssh/id_rsa.pub ram@client.itzgeek.local
Output:
ADVERTISEMENT
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/home/raj/.ssh/id_rsa.pub" The authenticity of host 'client.itzgeek.local (192.168.0.20)' can't be established. ECDSA key fingerprint is SHA256:z4TLSbno9MLNF1ucNq4gtMlLQDVgrfLKEt8JguchKdo. Are you sure you want to continue connecting (yes/no)? yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys ram@client.itzgeek.local's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh 'ram@client.itzgeek.local'" and check to make sure that only the key(s) you wanted were added.
Copying Keys Manually
Generate Public Key
This method involves generating an SSH key pair on the source machine and place it on the destination machine by login into it manually.
First, login into the source machine and create an SSH key pair using the following command.
[raj@server ~]$ ssh-keygen
Output:
Generating public/private rsa key pair. Enter file in which to save the key (/home/raj/.ssh/id_rsa): Created directory '/home/raj/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/raj/.ssh/id_rsa. Your public key has been saved in /home/raj/.ssh/id_rsa.pub. The key fingerprint is: SHA256:8BuI21rECULGQMs3BtU2o3jHyHghg+p5RE8naQTQP2A raj@server.itzgeek.local The key's randomart image is: +---[RSA 2048]----+ |+**o+.. | |o=+E X . | |.oX+& * | |.ooO.X = | |. = o * S | | o . + o | | . . o . | | o | | . | +----[SHA256]-----+

Once you have created, you will find two files id_rsa and id_rsa.pub inside the .ssh directory. We are going to use id_rsa.pub (public key) for SSH passwordless login.
[raj@server ~]$ ls -al ~/.ssh/
Output:
total 8 drwx------. 2 raj raj 38 Nov 7 21:50 . drwx------. 3 raj raj 74 Nov 7 21:50 .. -rw-------. 1 raj raj 1831 Nov 7 21:50 id_rsa -rw-r--r--. 1 raj raj 406 Nov 7 21:50 id_rsa.pub

Copy Public Key
You can use the scp command to copy the id_rsa.pub to the destination or copy the content of the id_rsa.pub file and paste it in ~/.ssh/authorized_keys file of the destination machine.
Method 1
Log in to the destination machine and create the .ssh directory in the home directory of the user, if it doesn’t exist.
[ram@client ~]$ mkdir ~/.ssh [ram@client ~]$ chmod 700 ~/.ssh
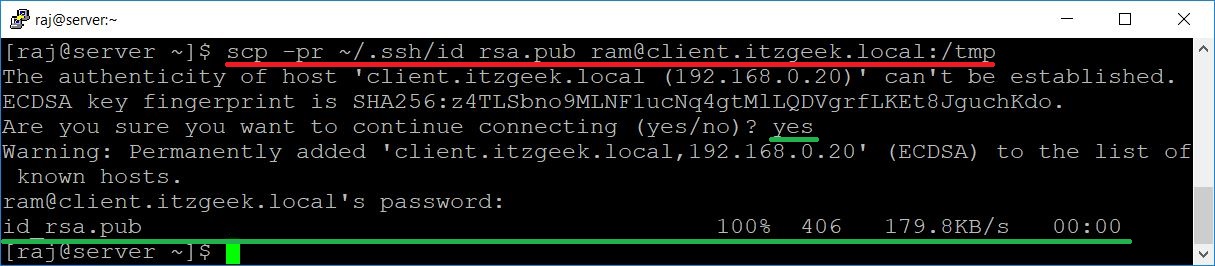
Use the scp command to copy the id_rsa.pub to the destination machine’s /tmp directory.
[raj@server ~]$ scp -pr ~/.ssh/id_rsa.pub ram@client.itzgeek.local:/tmp
You would need to enter the password for the destination as we are yet to configure the passwordless login.
Place the public key to the authorized_keys file for passwordless login.
[ram@client ~]$ cat /tmp/id_rsa.pub >> ~/.ssh/authorized_keys
Update the permission of the file.
[ram@client ~]$ chmod 600 ~/.ssh/authorized_keys
Method 2
Log in to the destination machine and create a .ssh directory in the home directory of the user, if it doesn’t exist.
[ram@client ~]$ mkdir ~/.ssh [ram@client ~]$ chmod 700 ~/.ssh
Edit the authorized_keys file.
[ram@client ~]$ vi ~/.ssh/authorized_keys
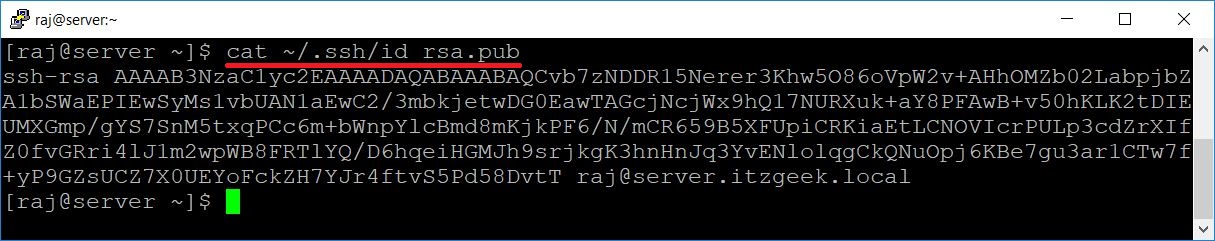
On the source machine, view the content of the id_rsa.pub file using the cat command.
[raj@server ~]$ cat ~/.ssh/id_rsa.pub
Output: (Sample)
Copy the content and past it into the authorized_keys file on the destination and save it.
ADVERTISEMENT
Then, update the permission of the file.
[ram@client ~]$ chmod 600 ~/.ssh/authorized_keys
Test Passwordless Login
Now access the remote machine using the ssh command.
[raj@server ~]$ ssh ram@client.itzgeek.local
Now, you should be able to access the remote machine without the password.
Conclusion
That’s All. I hope you are able to setup SSH passwordless login on CentOS 8 / RHEL 8. Please share your feedback in the comments section.