In our previous article, we set up OpenLDAP server on CentOS 7 / RHEL 7 for centralized authentication. In continuation to that, we will now configure OpenLDAP with SSL for secure communication. In this setup, LDAP clients communications happen over secure port 636 instead of nonsecure port 389.
Follow this guide to configure OpenLDAP with SSL.
Prerequisites
Contents
1. OpenLDAP Setup.
2. Make an host entry of LDAP server on your client machines in /etc/hosts for name resolution.
192.168.1.10 server.itzgeek.local server
OR
If you plan to use the hostname instead of IP address, then Configure DNS Server on CentOS 7 / RHEL 7 to have hostname resolution.
Create LDAP certificate
If you are planning to use LDAP over SSL, you can follow any of the below methods to implement it.
1. Self-signed certificate – It is a simple self-signed certificate. LDAP clients need to have tls_reqcert allow in /etc/nslcd.conf to not to validate the certificate.
2. CA-signed certificate – Your internal CA or external CA sign certificates. You should place the CA certificate that signed your LDAP server certificate in /etc/openldap/cacerts/ directory so that LDAP clients can validate certificates.
Self-Signed Certificate
Let’s create a self-signed certificate for our LDAP server. The below command generates both certificate and private key in /etc/openldap/certs/ directory.
openssl req -new -x509 -nodes -out /etc/openldap/certs/itzgeekldap.crt -keyout /etc/openldap/certs/itzgeekldap.key -days 1460
Output:
Generating a 2048 bit RSA private key ...+++ .....................................+++ writing new private key to '/etc/openldap/certs/itzgeekldapkey.pem' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]: XX State or Province Name (full name) []: XX Locality Name (eg, city) [Default City]: XXXXXX Organization Name (eg, company) [Default Company Ltd]:ITzGeek Organizational Unit Name (eg, section) []:IT Infra Common Name (eg, your name or your server's hostname) []:server.itzgeek.local Email Address []:admin@itzgeek.com
Set the owner and group permissions.
chown -R ldap:ldap /etc/openldap/certs/itzgeek*
Verify the created LDAP certificate under /etc/openldap/certs/ directory.
ll /etc/openldap/certs/itzgeek*
Output:
-rw-r--r--. 1 ldap ldap 1302 Apr 1 14:18 /etc/openldap/certs/itzgeekldap.crt -rw-r--r--. 1 ldap ldap 1704 Apr 1 14:18 /etc/openldap/certs/itzgeekldap.key
Create certs.ldif file to configure LDAP to use secure communication using a self-signed certificate.
ADVERTISEMENT
vi certs.ldif
Use the below information.
dn: cn=config changetype: modify replace: olcTLSCertificateFile olcTLSCertificateFile: /etc/openldap/certs/itzgeekldap.crt dn: cn=config changetype: modify replace: olcTLSCertificateKeyFile olcTLSCertificateKeyFile: /etc/openldap/certs/itzgeekldap.key
Import the configurations to LDAP server.
ldapmodify -Y EXTERNAL -H ldapi:/// -f certs.ldif
Verify the configuration
slaptest -u
You should get the following message on successful verification.
config file testing succeeded
Custom CA-Signed Certificate
Create the root key using the following command.
cd /etc/openldap/certs/ openssl genrsa -out itzgeekrootCA.key 2048
Now, create the self-signed root certificate.
openssl req -x509 -new -nodes -key itzgeekrootCA.key -sha256 -days 1024 -out itzgeekrootCA.pem
Output:
You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:XX State or Province Name (full name) []:XXX Locality Name (eg, city) [Default City]:XXX Organization Name (eg, company) [Default Company Ltd]:ITzGeek Organizational Unit Name (eg, section) []:XXX Common Name (eg, your name or your server's hostname) []:ITzGeek Root CA Email Address []:admin@itzgeek.com
Create a private key for LDAP server.
openssl genrsa -out itzgeekldap.key 2048
One you have the private key, create a certificate signing request.
openssl req -new -key itzgeekldap.key -out itzgeekldap.csr
Output:
Make sure the common name matches your LDAP server hostname or IP Address.
Generating RSA private key, 2048 bit long modulus .........+++ .............................................................+++ e is 65537 (0x10001) [root@server certs]# openssl req -new -key itzgeekldap.key -out itzgeekldap.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:XX State or Province Name (full name) []:XX Locality Name (eg, city) [Default City]:XXX Organization Name (eg, company) [Default Company Ltd]:ITzGeek Organizational Unit Name (eg, section) []:IT Common Name (eg, your name or your server's hostname) []:server.itzgeek.local Email Address []:admin@itzgeek.com Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Now, sign a certificate signing request using the custom root CA.
openssl x509 -req -in itzgeekldap.csr -CA itzgeekrootCA.pem -CAkey itzgeekrootCA.key -CAcreateserial -out itzgeekldap.crt -days 1460 -sha256
Set the owner and group permissions.
chown -R ldap:ldap /etc/openldap/certs/itzgeek*
Verify the created LDAP certificate under /etc/openldap/certs/ directory.
ll /etc/openldap/certs/itzgeek*
Output:
ADVERTISEMENT
-rw-r--r--. 1 ldap ldap 1285 Apr 1 16:54 /etc/openldap/certs/itzgeekldap.crt -rw-r--r--. 1 ldap ldap 1050 Apr 1 16:53 /etc/openldap/certs/itzgeekldap.csr -rw-r--r--. 1 ldap ldap 1675 Apr 1 16:51 /etc/openldap/certs/itzgeekldap.key -rw-r--r--. 1 ldap ldap 1679 Apr 1 16:49 /etc/openldap/certs/itzgeekrootCA.key -rw-r--r--. 1 ldap ldap 1399 Apr 1 16:49 /etc/openldap/certs/itzgeekrootCA.pem -rw-r--r--. 1 ldap ldap 17 Apr 1 16:54 /etc/openldap/certs/itzgeekrootCA.srl
Create certs.ldif file to configure LDAP to use secure communication using a self-signed certificate.
vi certs.ldif
Use the below information.
dn: cn=config changetype: modify replace: olcTLSCACertificateFile olcTLSCACertificateFile: /etc/openldap/certs/itzgeekrootCA.pem dn: cn=config changetype: modify replace: olcTLSCertificateFile olcTLSCertificateFile: /etc/openldap/certs/itzgeekldap.crt dn: cn=config changetype: modify replace: olcTLSCertificateKeyFile olcTLSCertificateKeyFile: /etc/openldap/certs/itzgeekldap.key
Import the configurations to LDAP server.
ldapmodify -Y EXTERNAL -H ldapi:/// -f certs.ldif
Verify the configuration
slaptest -u
You should get the following message on successful verification.
config file testing succeeded
Configure OpenLDAP to listen over SSL
Edit the /etc/sysconfig/slapd file and configure OpenLDAP to listen over SSL.
vi /etc/sysconfig/slapd
Update the below line.
SLAPD_URLS="ldapi:/// ldap:/// ldaps:///"
Restart the slapd service.
systemctl restart slapd
Verify the LDAP service. LDAP service should now be listening on TCP port 636 as well.
netstat -antup | grep -i 636
Output:
tcp 0 0 0.0.0.0:636 0.0.0.0:* LISTEN 11720/slapd tcp6 0 0 :::636 :::* LISTEN 11720/slapd
Firewall
Add the LDAPS service to the firewall (TCP 686).
firewall-cmd --permanent --add-service=ldaps firewall-cmd --reload
OpenLDAP client configuration for OpenLDAP over SSL
Install the client packages using the yum command.
yum install -y openldap-clients nss-pam-ldapd
Execute the authconfig command to add a client machine to LDAP server for single sign-on. Replace “server.itzgeek.local” with your LDAP server’s IP address or hostname.
If you have used Custom CA-singed or external CA-signed certificate in OpenLDAP setup, then the Hostname or IP address should match with the common name of the LDAP server certificate
authconfig --enableldap --enableldapauth --ldapserver=ldaps://server.itzgeek.local --ldapbasedn="dc=itzgeek,dc=local" --enablemkhomedir --disableldaptls --update
You would need to perform the below steps based on the method you have configured OpenLDAP to use SSL.
ADVERTISEMENT
Self-Signed Certificate
Edit the nslcd.conf file.
vi /etc/nslcd.conf
Add the following line in the nslcd.conf file. The below setting will disable the certificate validation done by clients as we are using a self-signed certificate.
tls_reqcert allow
Custom CA-Signed or External CA Signed
Copy the itzgeekrootCA.pem from LDAP server or place the intermediate certificate or CA provided by external CA in the /etc/openldap/cacerts directory.
cd /etc/openldap/cacerts/ scp -pr 192.168.1.10:/etc/openldap/certs/itzgeekrootCA.pem /etc/openldap/cacerts
Create the c hash of the CA certificate.
/etc/pki/tls/misc/c_hash /etc/openldap/cacerts/itzgeekrootCA.pem
Output:
997ee4fb.0 => /etc/openldap/cacerts/itzgeekrootCA.pem
Now, symlink the rootCA.pem to the shown 8 digit hex number.
ln -s /etc/openldap/cacerts/itzgeekrootCA.pem 997ee4fb.0
Restart the LDAP client service.
systemctl restart nslcd
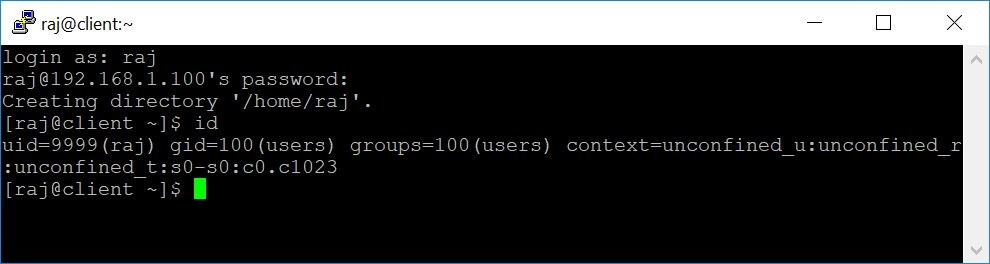
Verify LDAP Login
Use getent command to get the LDAP entries from the LDAP server.
getent passwd raj
Output:
raj:x:9999:100:Raj [Admin (at) ITzGeek]:/home/raj:/bin/bash
To verify the LDAP, log in using the LDAP user “raj” on the client machine.
Screenshot:
Reference
OpenFusion – OpenLDAP Tips and Tricks
CentOS – Forum
That’s All.