This post originally appeared on Clouds, etc. by Daniel Paluszek.
Read Continuation of vCD Extender – Warm Migration Setup – 1 of 2
3. Configure L2 Appliance configuration inside of tenant Extender Appliance
Alright, now we are ready to set up the DC Extension on the tenant side. First, we need to tell the tenant Extender appliance where to position the L2VPN-Client edge in the tenant environment.
First, let’s log into the Extender tenant appliance:
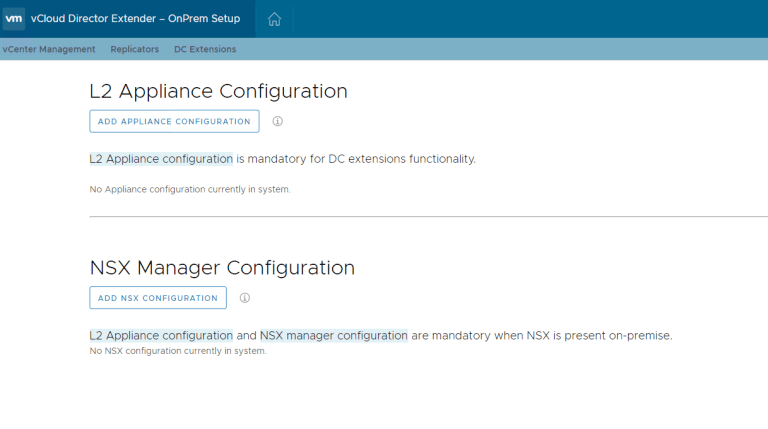
Click on DC Extensions and Add Appliance Configuration (top button) – remember, our tenant does not have NSX (but could as you see below!) so we will have Extender deploy a standalone L2VPN Client edge.
Now let’s put in the configuration parameters for the L2 Appliance. As you can see, this is for my “Company-Network” so I set its IP, default GW, and the prefix length. Make sure you hit the Add button before hitting Create:
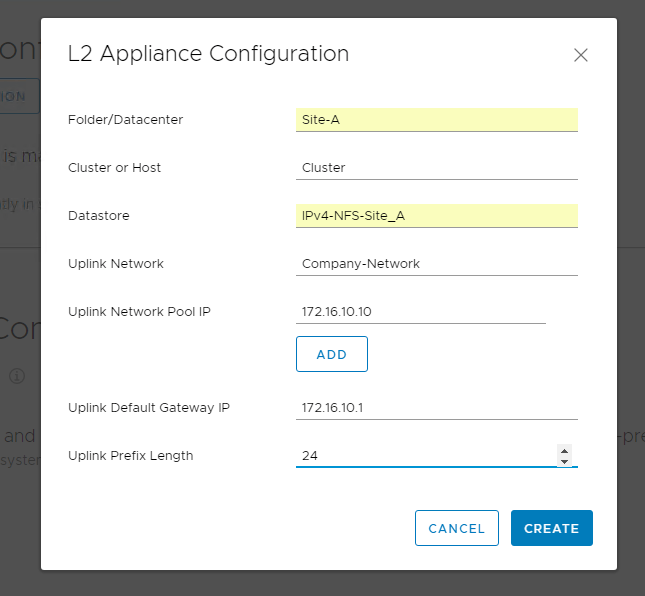
Ok, great, now we have an L2 Appliance Configuration:
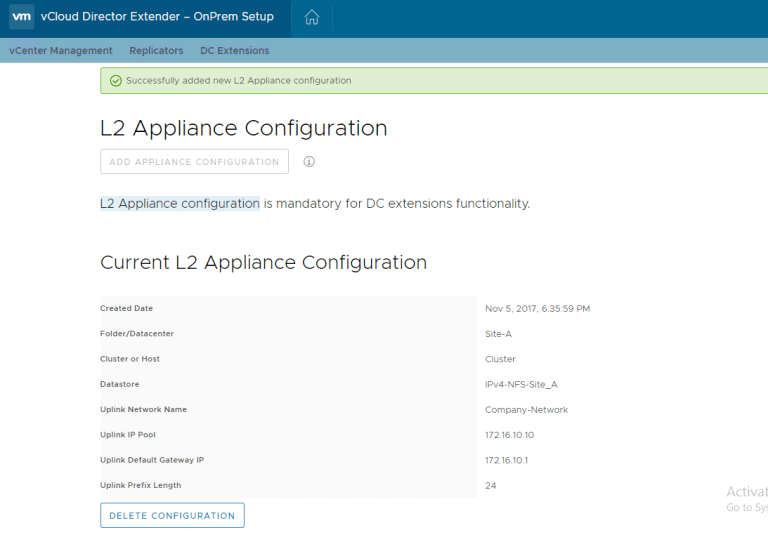
Next, let’s get into the Plugin and establish our DC Extension.
4. Establish DC Extension in Extender plugin
Last step before we can start migrating! This is assuming you have your provider cloud established – let’s now go to DC Extensions
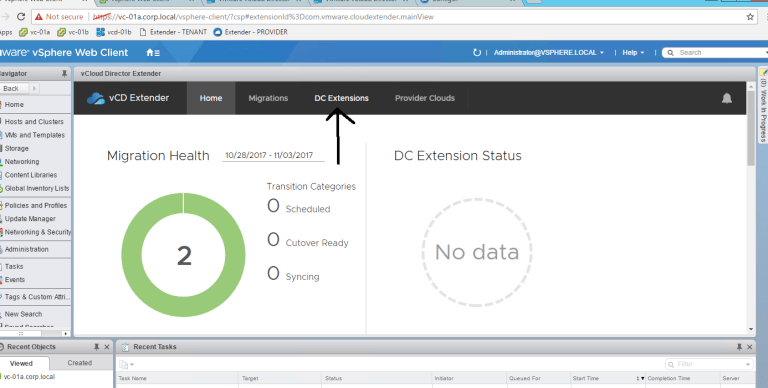
Click on New Extension –
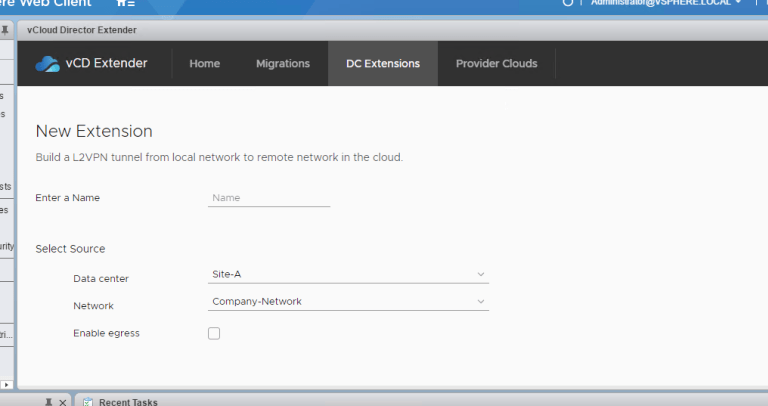
Put in a name, source info (you can see I selected my Company-Network) and Destination will populate your vDC along with the subinterface Network. If you do not see any Network, something went awry with the trunk interface, check it out.
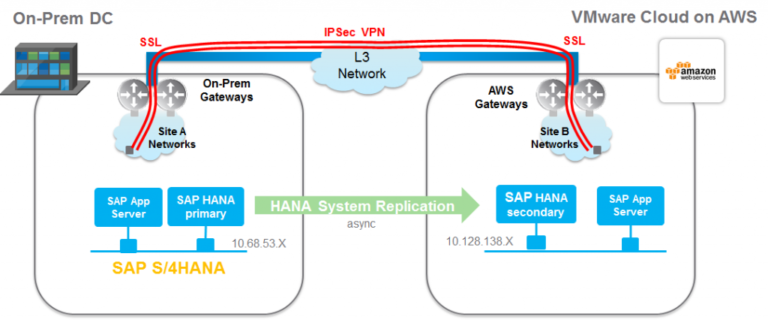
Also, note that we added the local Egress default gateway IP to enable the L2VPN-Client to route any packets sent towards the Egress Optimization IP address locally, and send everything else over the tunnel. If the default gateway for the virtual machines (belonging to the subnets you’re stretching) is same across the two sites you will need this setting to ensure traffic will be locally routed on each site. Should you need to migrate VM from one site to the other, you can do so without changing the network configuration on the guest VM and hence the mobility.
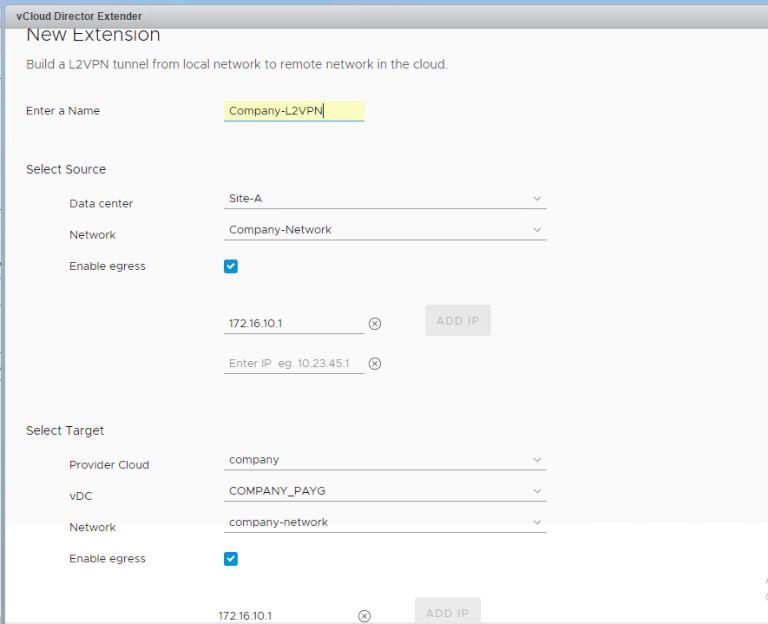
Now click that Start button…
Now we will see the status as Connecting…
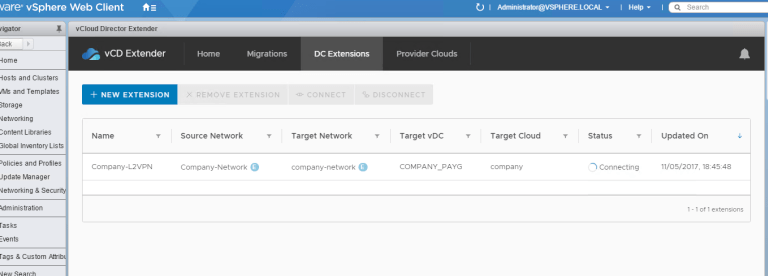
So what’s happening in the background? Well, Extender is now deploying the L2VPN standalone edge and also creating a Distributed Port Group for the sink traffic:
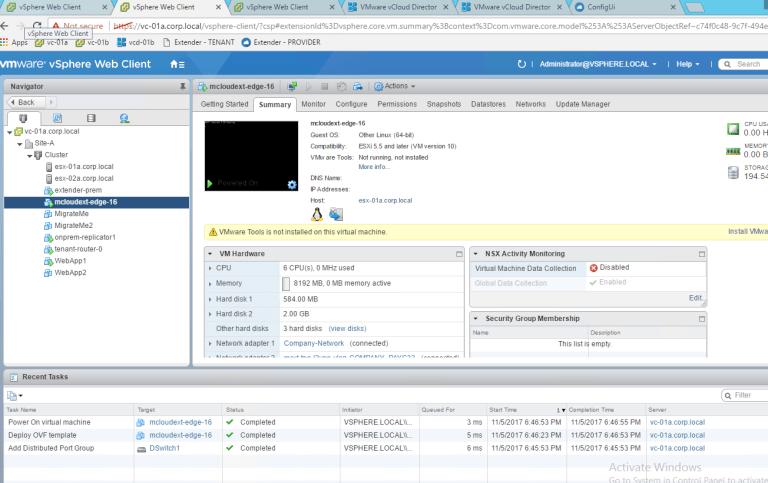
On the Provider side, what do we have here? We have a new site config under the L2VPN-Server:
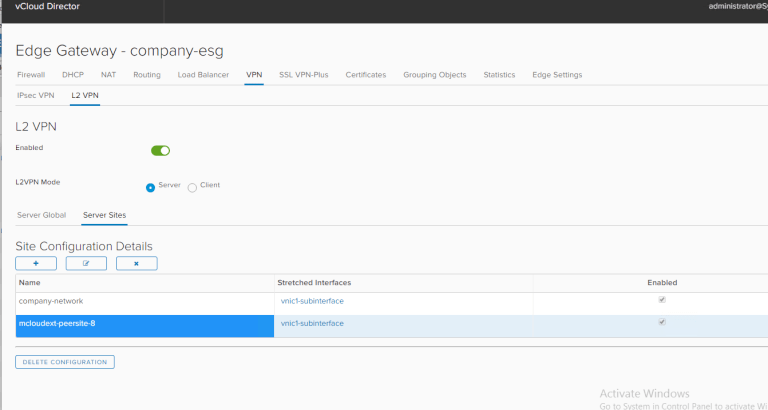
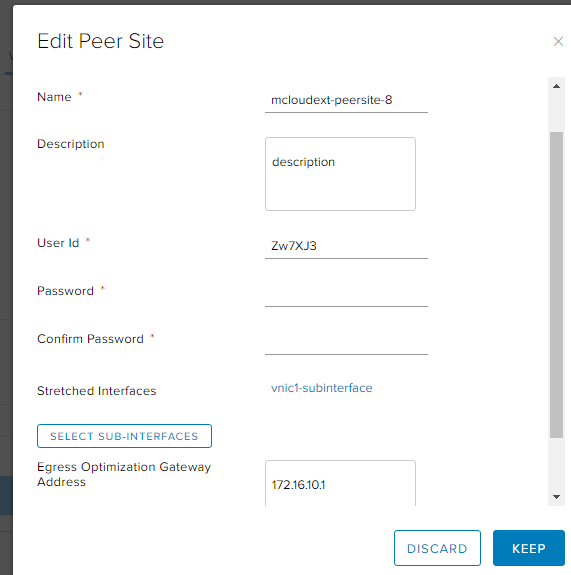
Really slick! So Extender automatically creates a new config based on this configuration.
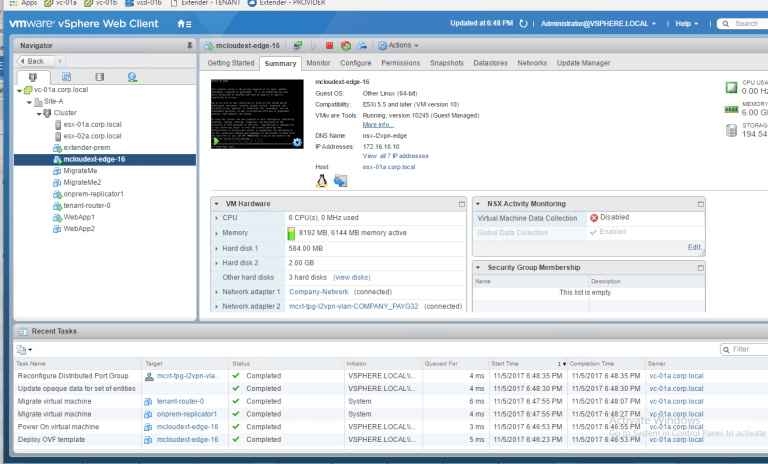
Going back to the tenant, I see the IP was set to the L2VPN-Client Edge and the sink port was configured completely:
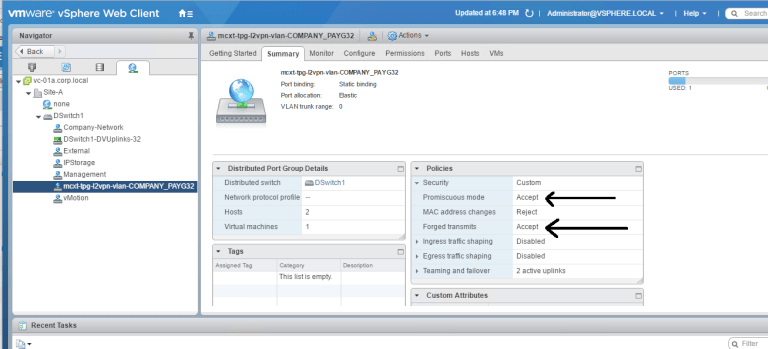
Taking a closer look at the DVS port Extender created, we can see Promiscuous Mode and Forged Transmits were set to Accept:
Oh, and look at that – it’s Connected! Woohoo!!!
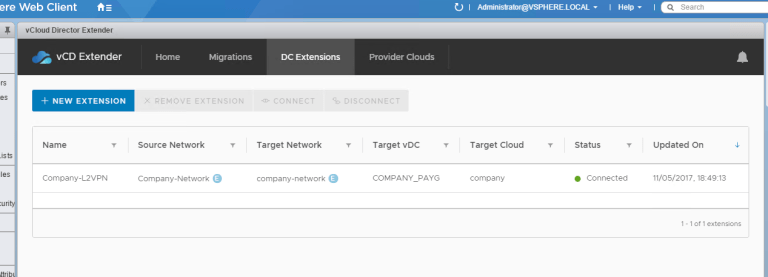
On the Provider NSX side, we can see the tunnel is up and kicking:
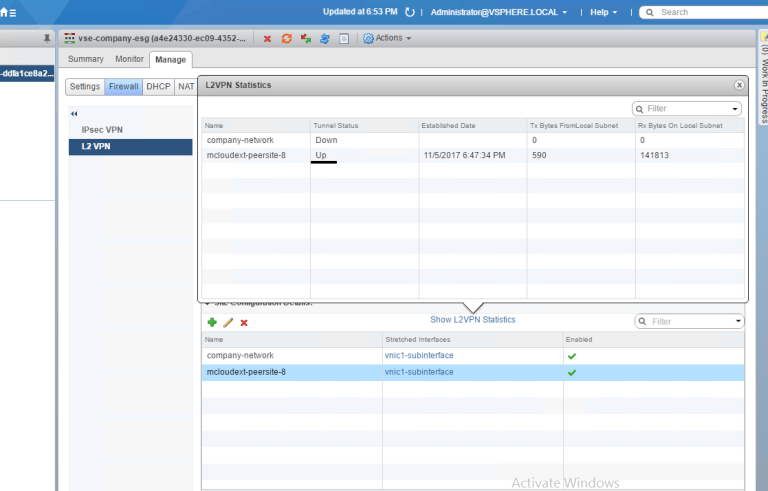
COMPLETE! You are now ready for your first warm migration.
Again, big thanks to my buddy Wissam for the collaboration here.
Stay tuned to the VMware Cloud Provider Blog for future updates, and be sure to follow @VMwareCloudPrvdon Twitter and ‘like’ us on Facebook.