How to Fix WordPress Memory Exhausted Error Increase PHP Memory
Have you ever encountered the “memory size exhausted” message on your website? If yes, then you’ll…
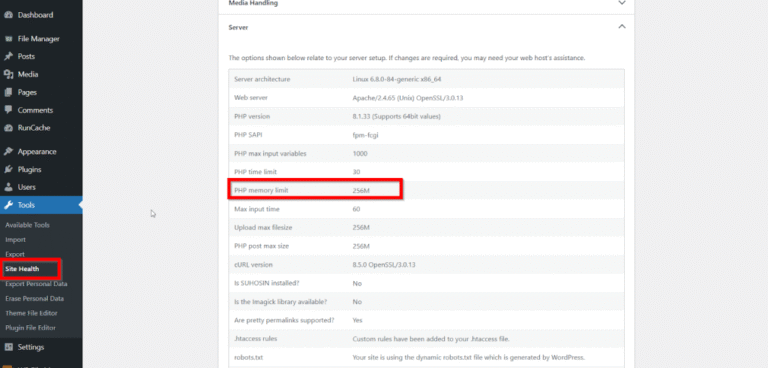
Have you ever encountered the “memory size exhausted” message on your website? If yes, then you’ll…
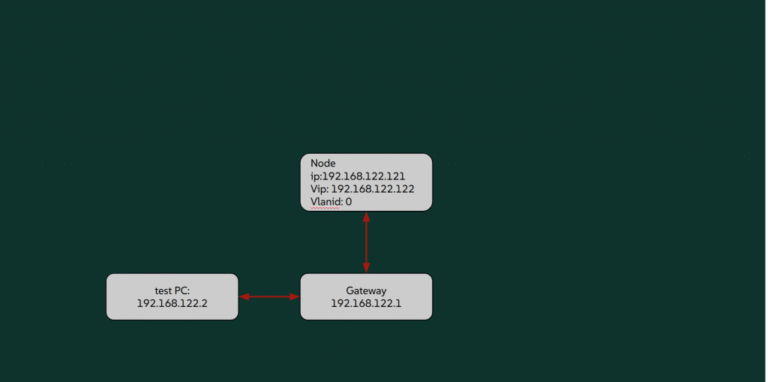
SUSE Virtualization (also known as Harvester) offers versatile networking options for VMs to use. In this…

CloudLinux is implementing a pricing adjustment for CloudLinux OS Legacy licenses. Beginning January 1, 2026, pricing…

We’re pleased to launch the latest milestone in our journey: CloudLinux OS 10.1 Stable Release! This…
Today’s software applications require developers, testers, and SysAdmins to work together (DevSecOps) more seamlessly than ever…
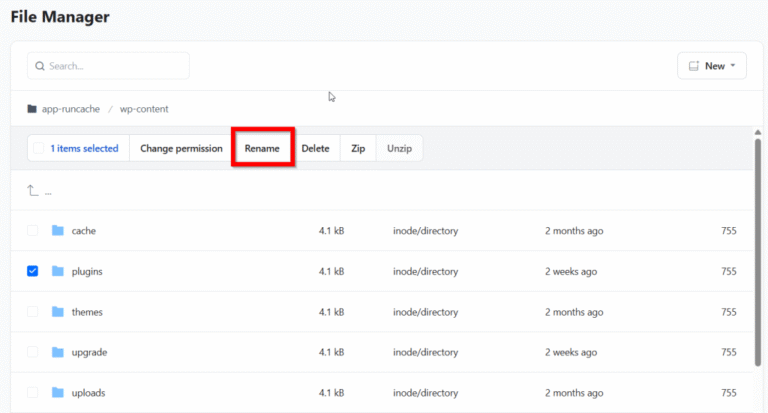
Have you ever opened a website and been greeted with a blank page instead of the…
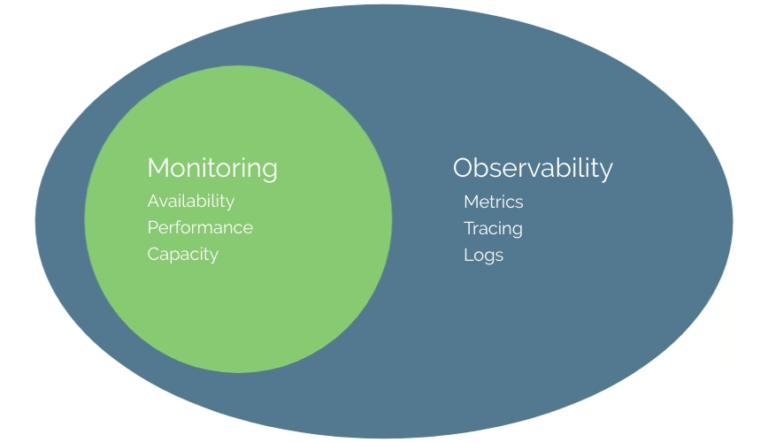
Previously we’ve covered the future of APM (application performance monitoring) and the expansion of APM into observability….

Observability and AI Artificial Intelligence (AI) s a set of techniques, methods, and strategies that lets…

We’re pleased to unveil the latest milestone in our journey: CloudLinux OS 9.7 Stable Release! This…

Today, we are thrilled to announce CloudLinux’s strategic investment in Seahawk, a leading provider of white-label,…
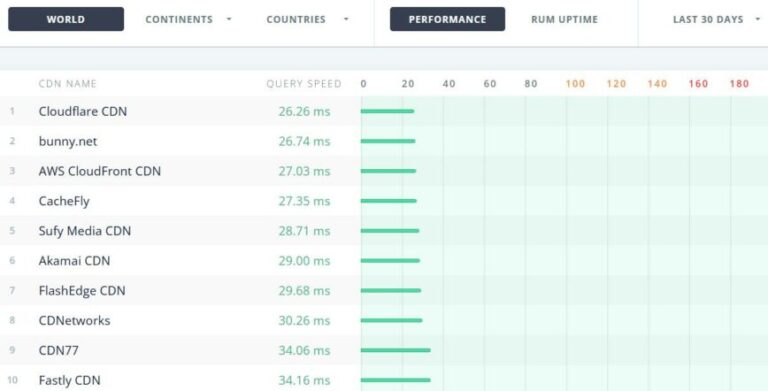
A content delivery network, also referred to as a content distribution network (CDN), is a geographically distributed network of data…
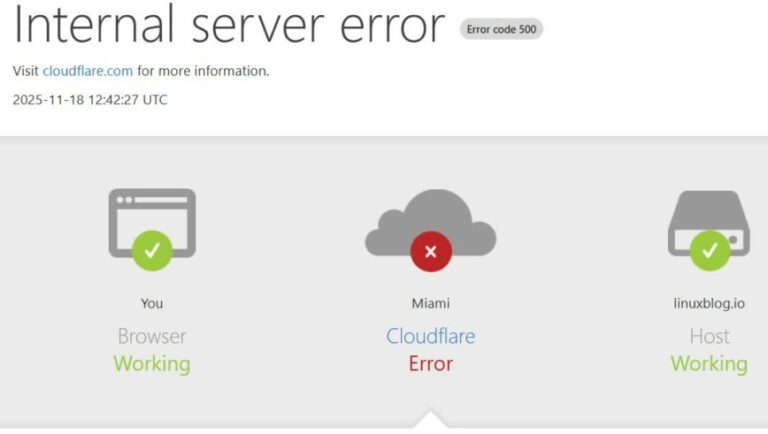
Cloudflare is one of those companies most people never think about, yet on mornings like this…
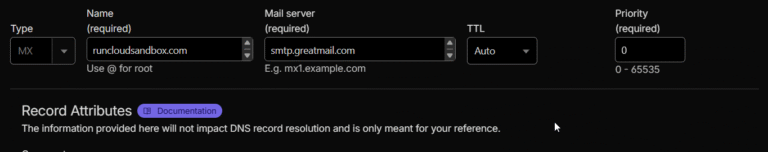
As a RunCloud user, you already know how to manage high-performance websites and servers efficiently. But…

Over time, tool sprawl has become the default state of enterprise security. Many organizations run dozens…
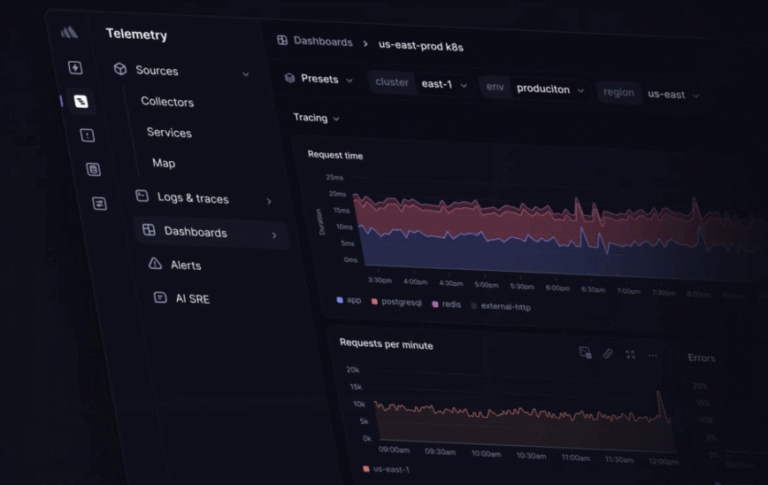
Looking for application monitoring and observability solutions? On this page, I’ve listed the top application performance…

In the market for a multi‑gigabit firewall/router, two names come up repeatedly: Firewalla Gold Plus and…
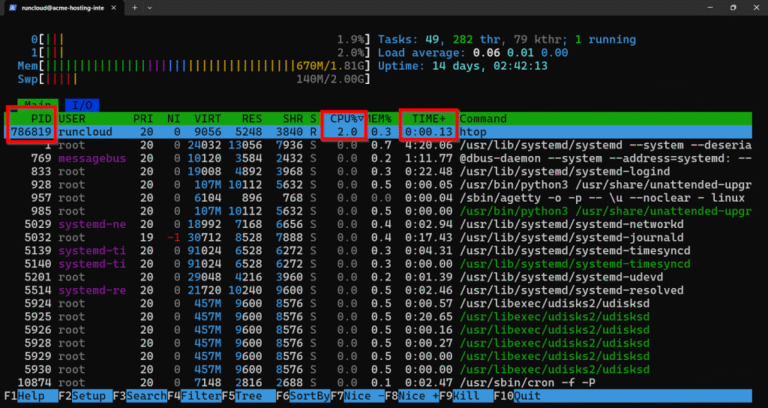
Is your Linux server slowing down? CPU usage is often the reason. Monitoring CPU performance helps…
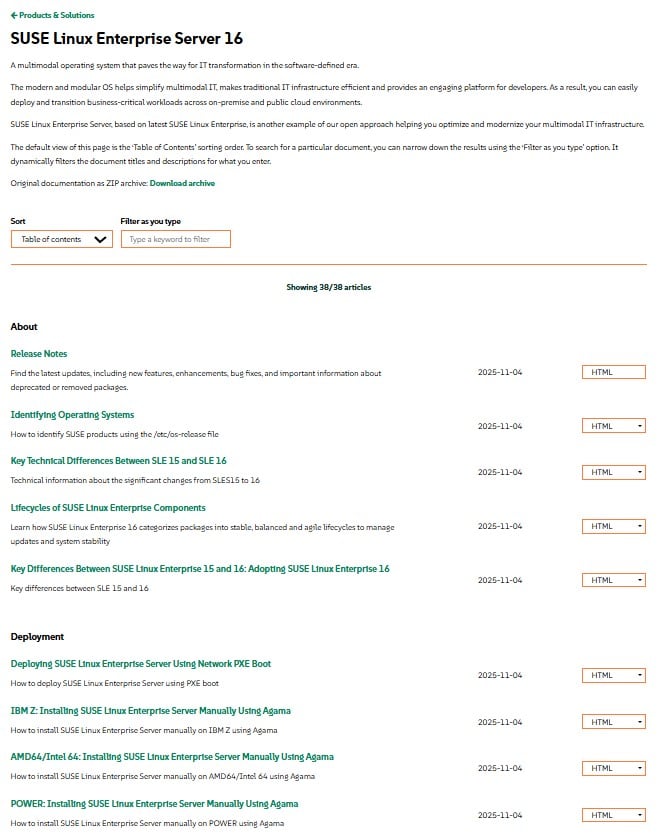
I’m sure you’ve read the recent exciting announcement about the general availability of SUSE Linux Enterprise…

Every year, like clockwork, Black Friday turns the hosting world into a price war. Inboxes fill…
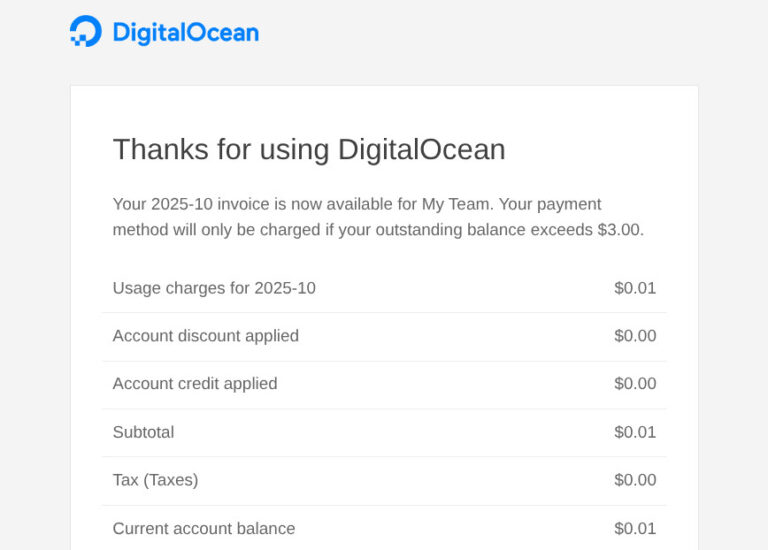
There are three kinds of emails that can ruin a quiet Saturday: a security warning, an…
If your website goes down, every second counts. Uptime monitoring tools alert you before visitors or…